| OSI Model Layer Responsibilities | |
| TCP/IP Model Responsibilities | |
| TCP/IP Protocol Suite | |
| Network Data Flow |
Like every network protocol, TCP/IP has an underlying specific architectural design that makes it function properly. In this chapter we focus on TCP/IP architecture and learn the details of how it works. In the first section, we will discuss the responsibilities of each layer in the Open System Interconnect (OSI) model and in the second section we discuss the TCP/IP model. Next, we will compare the TCP/IP protocol stack to the OSI model. Then we will examine which TCP/IP protocols operate at different levels within the TCP/IP model. Finally, we put it all together and examine how data flows through a network.
Back when networking was a new concept and only starting to be implemented in businesses, it was common to install equipment from different vendors only to find that it could not communicate with each other. This was because each vendor used their own method for communication, and it was highly unlikely that an application operating on equipment from one vendor would be able to communicate with equipment from other vendors. It didn’t take long for vendors and users to see the need for a standard architecture so that network communication could take place between multiple vendors’ equipment.
The members of the International Standards Organization (ISO) are from various companies, industries, and countries. Among other things, they are responsible for creating, maintaining, and implementing standards for hardware and software. ISO introduced a set of specifications in 1978 to standardize the architecture used to communicate on a network using devices from different vendors. In 1984, ISO revised the specifications and released it with the name Open Systems Interconnect (OSI) model. The OSI model is the best known and most widely used set of specifications used by vendors when they design equipment for networking environments.
The OSI model consists of seven layers, as shown in Figure 2-1. A common mnemonic to help you remember the layers from top to bottom is, "All People Seem To Need Data Processing." There are many more phrases, and you can always invent your own. Each of the seven layers of the OSI model exists as an independent module and performs a well-defined function as described later in this section. All the layers in the OSI model work in a hierarchy. If a computer is sending data, each layer receives the data from the layer above it, performs any applicable work on that data, and adds on its own information regarding that data. The layer then sends the data on down to the next layer. If a computer is receiving data, each layer receives data from the layer below it, strips away the applicable data, and passes it on to the next higher layer.
Each layer communicates and works with the functions of the layers that are immediately above and below it. For example, looking at Figure 2-1, you see that the Network layer sits between the Transport and Data Link layers. This means that the Network layer will communicate and work with both the Transport and Data Link layers. The Network layer cannot communicate directly with any other layer of the OSI model.
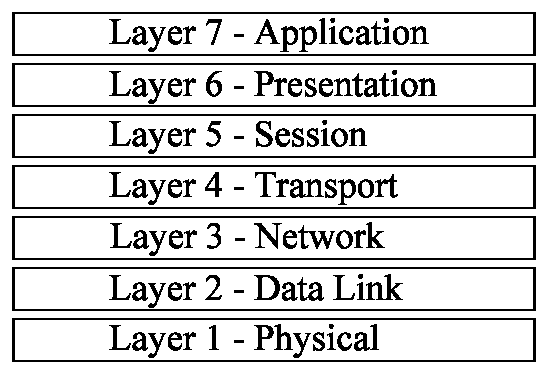
Figure 1: OSI Model Layer Stack Showing the Seven Layers
The layers are strategically organized. The higher the layer resides in the model, the more complex the task it performs. Each layer is separated from the layers on each side of it by an interface, which defines which services are offered and how they will be accessed. Data passes from one layer, through the interface, to the next layer where additional processing is performed as necessary. The layers are organized so that it seems like each layer is communicating with the same layer on another computer using virtual communication as shown in Figure 2-2. However, communication is actually taking place between neighboring layers on only one computer.
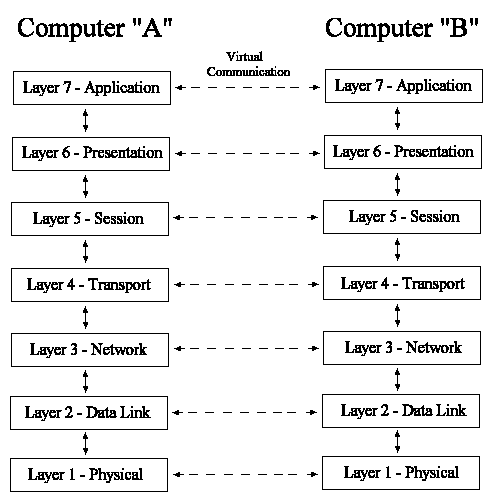
Figure 2: OSI Layer Relationships
As data passes from one layer to the next layer, additional formatting or addressing is added from the sending computer so that it can be transmitted successfully. When the data arrives at the receiving computer, the data passes through the layers in reverse order. Formatting and addressing information is stripped away at each layer as it is passed up the layers until it arrives at the seventh layer, the Application layer, where it is returned back to its original state that can be interpreted by the receiving computer.
We say that each layer is dedicated only to its own task and is unaware of the responsibilities of the layers above and below it.
To understand the layers model used by OSI and TCP/IP, let’s look at an example from real life.
You and some friends start a company. You get together and think through the things that must be done. You answer questions such as:
| What needs to be done? | |
| In what order will they be done? | |
| Who will do these things? | |
| How do they relate or interact with each other? |
After spending hours of brainstorming, you group these tasks into departments.
Each department has its own task list and you require that it focus only on that particular task. Each department will have to trust and rely on the other departments to do their designated tasks.
Similarly, OSI and TCP/IP layers are designed and implemented just like your hypothetical departments; that is, they are concerned only with their own specific tasks.
The only OSI layer that can communicate directly with its equivalent on another computer system is Layer 1, the Physical layer. All other layers must communicate down the layers from the sending computer, across the media, and up the layers on the receiving computer. For example, if the Network layer had information for the Network layer of another computer system it would go from the Network layer to the Data Link and Physical layers of the sending computer, across the media, then up the Physical and Data Link layers to the Network layer of the receiving computer.
We will now discuss the purpose of each layer in the OSI model.
The Application layer is the top layer of the OSI model. It is used to allow applications to access network services. It handles general network access, flow control, and error recovery. Some of the functions it supports are:
| Accessing remote files | |
| Accessing remote printers | |
| Accessing remote databases | |
| Electronic mail |
The next layer down is the Presentation layer which is located at layer 6. It is the translator for the network as it determines the format used to exchange data among the computers on the network. Some of its functions are:
| Protocol conversion | |
| Data translation | |
| Data encryption | |
| Data compression | |
| Conversion of the character set |
Layer 5 is the Session layer, which establishes a communications connection between processes running on different computers. It performs name recognition and related functions; for example, user authentication and resource-access security that are needed to allow processes to communicate over the network. To ensure that all data gets sent, it uses checkpoints placed in the data stream to provide for synchronization. In the case of network failure the only data that needs to be sent again is the data after the last checkpoint. The Session layer is also responsible for controlling when and for how long each side transmits.
Layer 4 is the Transport layer, which is responsible for ensuring that all the data is delivered in the correct sequence, error free, with no losses. It is the Transport layer that breaks up large messages into smaller packets for delivery. Some of the other functions provided by the Transport layer are:
| Error handling | |
| Flow control by notifying the transmitting computer to not transmit when the receiving computer has no available receive buffers |
Layer 3, the Network layer, is responsible for determining the route that is taken from the transmitting computer to the receiving computer. It is also responsible for addressing messages and the translation of logical addresses into physical addresses. The Network layer determines what path the data should take based upon several factors, including the condition of the network and the priority of service.
Layer 2 is the Data Link layer, which is responsible for providing error-free transfer of frames from one computer to another using the Physical layer. A frame is a bundle of information sent as a single entity. Some of the other functions provided by the Data Link layer are:
| Transmitting and receiving frames sequentially | |
| Providing frame acknowledgment for frames it receives | |
| Retransmitting frames that are not acknowledged by the receiving computer |
The Physical layer is located at layer 1, the bottom of the OSI model. The Physical layer handles the unstructured, raw, bit-stream data that is transferred over a physical medium. It also defines how the physical medium, or cable, is attached to the Network Interface Card (NIC). It does that by determining how many pins are in the connector that is being used and also the function of each of the pins. The Physical layer sends out bits equaling 1s and 0s and determines how long each bit lasts and how it is translated into the suitable optical or electrical impulse for the network cable.
The TCP/IP model was not created by a standards developing committee but rather from research funded by the Department of Defense (DOD) Advanced Research Projects Agency (ARPA). ARPA begin working on TCP/IP technology in the mid 1970s with the protocols and architecture taking on their current structure in the 1977-1979 time frame.
The TCP/IP protocol stack is organized into four layers as shown in Figure 2-3. Each of the four layers of the TCP/IP model exists as an independent module and performs a well-defined function as described later in this section. Each layer communicates and works with the functions of the layers that are immediately above and below it. For example, looking at Figure 2-3 you see that the Transport layer sits between the Application and Internet layers. This means that the Transport layer will communicate and work with both the Application and Internet layers. The Transport layer cannot communicate directly with any other layer of the TCP/IP model.
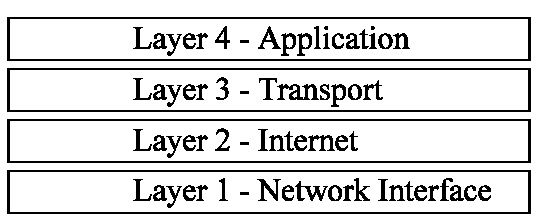
Figure 3: TCP/IP Protocol Stack
The Application layer is the highest layer in the TCP/IP model. It is used by applications to access services across a TCP/IP network. Some of the applications that operate at this layer are a Web browser, file transfer program (FTP), and a remote login program. The Application layer passes data to the next layer in the stack, the Transport layer.
The Transport layer is located at layer 3 of the TCP/IP model. The main responsibility of the Transport layer is to provide communication from one application to another application. If several application programs are running on a computer then the Transport layer has to figure out how to control the data from each application so that it can be sent to the next lower layer correctly. The Transport layer adds the following additional information to each data packet:
| The identity of the application sending the data | |
| The identity of the application that should receive the data | |
| A checksum |
The system that receives the data uses the checksum to verify that all of the data arrived. It also uses the identity of the receiving application so it can route the data appropriately.
The Internet layer is located at layer two of the TCP/IP model. It is responsible for handling the communication from one computer to another computer. It accepts a request to send data from the Transport layer. It accepts the data, encapsulates it in a datagram, and then uses a routing algorithm to determine the best method for delivering it. After determining the best way to route the datagram, the Internet layer passes it to the Network Interface layer.
The Network Interface layer is the lowest level in the TCP/IP model. It accepts the datagram from the Internet layer and transmits it over the network. To accomplish this task the Network Interface layer must be fully aware of the network hardware that it is using. The Network Interface layer is also responsible for translating an Internet address into a hardware address.
The TCP/IP model can be compared loosely to the OSI model as shown in Figure 2-4. The Application layer of the TCP/IP model performs the same functions as layers 5, 6, and 7 of the OSI model. The Transport layers in both models perform the same functions. The Internet layer of the TCP/IP model equates to the same functions as the Network layer of the OSI model. The Network Interface layer of the TCP/IP model compares to the functions of layers 1 and 2 of the OSI model.
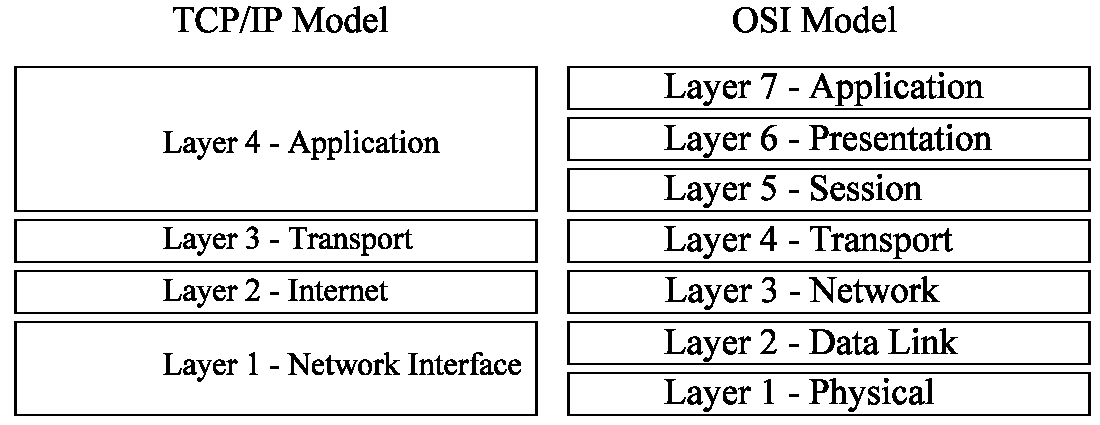
Figure 4: TCP/IP Model Compared to OSI Model
Contained within the four layers of the TCP/IP model are several protocols that direct how computers connect and communicate using TCP/IP. Even though the protocol suite is called TCP/IP, many other protocols are available besides the TCP and IP protocols.
Each protocol can be identified with a layer of the TCP/IP model. We will examine several of the protocols available at each layer.
The Application layer supports both the NetBIOS interface and the Windows Sockets interface.
NetBIOS over TCP/IP allows NetBIOS client and server applications to be run over the Wide Area Network (WAN). Some of the applications that are NetBIOS-over -TCP compliant are the Windows NT browser service, netlogon service, messenger service, workstation service, and server service.
Windows Sockets is a programming interface based on the "socket" interface that was originally developed at the University of California at Berkeley. Windows Sockets includes enhancements that take advantage of the message-driven characteristics of Windows. Windows NT 4.0 supports version 2.2.0, which was published in May 1996. Some of the common protocols that use Windows Sockets are telnet, ftp, and http.
The Transport layer consists of two protocols, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). Both TCP and UDP support ports. When a program sends or receives data on a TCP/IP network, it has to connect to a port. Ports are identified in the header of both the TCP and UDP protocols. The header contains two 16-bit numbers that identify the source port and the destination port. The Transport layer examines the port numbers in the header and delivers the data to the correct port.
TCP is one of the protocols that the suite is named for. TCP provides a reliable, connection-based delivery service. Successful delivery of packets is guaranteed by the TCP protocol. It uses a checksum to ensure that data is sequenced correctly. If a TCP packet is lost or corrupted during transmission, TCP resends a good packet. The reliability of TCP is necessary for critical services, such as electronic mail. However, the reliability does not come cheaply as TCP headers have additional overhead added to them. The overhead is necessary to guarantee successful delivery of the data. Another factor to remember about TCP is that the protocol requires the recipient to acknowledge the successful receipt of data. Of course, all the acknowledgments, known as ACKs, generate additional traffic on the network, which causes a reduction in the amount of data that is passed for a given time frame.
The TCP header consists of six words of 32 bits each. The seventh word is the actual data. Figure 2-5 shows the format of a TCP header.
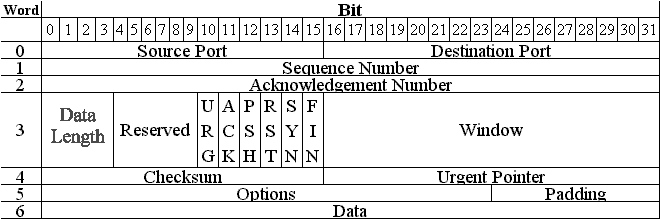
Figure 5: Transmission Control Protocol Header
Table 2-1 describes each of the items that are contained in the TCP header.
Name |
Bit Size |
Purpose |
Source Port |
16 |
The source port number. |
Destination Port |
16 |
The destination port number. |
Sequence Number |
32 |
The sequence number of the first data octet in this segment unless the SYN control bit is set. If the SYN control bit is set, then the sequence number is the initial sequence number (ISN) and the first data octet is ISN+1. |
Acknowledgment Number |
32 |
This portion of the header contains the value of the next sequence number that the sender of the segment is expecting to receive if the ACK control bit is set. Once a connection is established, this is always sent. |
Data Length |
4 |
The number of 32-bit words in the TCP header. This indicates where the data begins. |
Reserved |
6 |
Reserved for future use. It has to be zero. |
Flags |
6 |
The bits from left to right. URG: Urgent Pointer field significant ACK: Acknowledgment field significant PSH: Push function RST: Reset the connection SYN: Synchronize sequence numbers FIN: No more data from sender |
Window |
16 |
The number of data octets beginning with the one indicated in the acknowledgment field, which the sender of this segment is willing to accept. |
Checksum |
16 |
The checksum field is the 16-bit 1’s complement of the 1’s complement sum of all 16-bit words in the header and data. |
Urgent Pointer |
16 |
This field communicates the current value of the urgent pointer as a positive offset from the sequence number in this segment. The urgent pointer points to the sequence number of the octet following the urgent data. This field is interpreted only in segments that have the URG control bit set. |
Options |
variable |
Options may occupy space at the end of the TCP header and are a multiple of 8 bits in length. All options are included in the checksum. |
Padding |
variable |
The TCP header padding is used to ensure that the TCP header ends and data begins on a 32-bit boundary. The padding is composed of zeros. |
Table 1: Description of the Contents in a TCP Header
UDP offers a connectionless datagram service that is an unreliable "best effort" delivery. The arrival of datagrams is not guaranteed by UDP nor does it promise that the delivered packets are in the correct sequence. Applications that don’t require an acknowledgment of receipt of data use the User Datagram Protocol.
The UDP header consists of two words of 32 bits each. The third word is the actual data. Figure 2-6 shows the format of a UDP header.
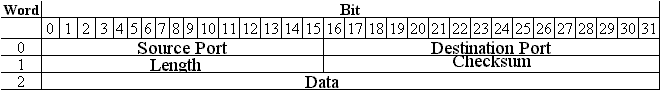
Figure 6: User Datagram Protocol Header
Table 2-2 describes each of the items that are contained in the UDP header.
Name |
Bit Size |
Purpose |
Source Port |
16 |
The source port number. |
Destination Port |
16 |
The destination port number. |
Length |
16 |
The length in octets of this user datagram including the header and data. |
Checksum |
16 |
The checksum field is the 16-bit 1's complement of the 1's complement sum of all 16-bit words in the header and data. The checksum is an option in the UDP header and not always used. |
Table 2: Description of the Contents in a UDP Header
The Internet layer consists of two protocols, the Internet Protocol (IP) and the Internet Control Message Protocol (ICMP).
IP is the other protocol that the suite is named for. It is a vital link in the suite as all information that is sent using the TCP/IP protocol suite must use it. IP provides packet delivery for all other protocols within the suite. It is a connectionless delivery system that makes a "best-effort" attempt to deliver the packets to the correct destination. IP does not guarantee delivery nor does it promise that the IP packets will be received in the order they were sent. IP does use a checksum but it confirms only the integrity of the IP header. Confirmation of the integrity of data contained within an IP packet can be accomplished only through higher level protocols.
The IP header consists of six words of 32 bits each. The seventh word is the actual data. Figure 2-7 shows the format of a IP header.
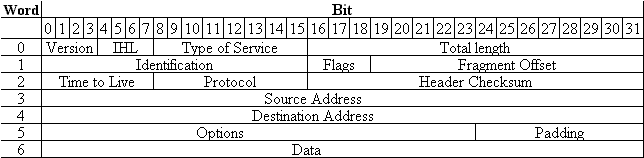
Figure 7: Internet Protocol Header
Table 2-3 describes each of the items that are contained in the IP header.
Name |
Bit Size |
Purpose |
Version |
4 |
The format of the Internet header. |
IHL |
4 |
Internet header length is the length of the Internet header in 32-bit words. The minimum value for a correct header is 5. |
Type of Service |
8 |
An indication of the abstract parameters of the quality of service desired. |
Total Length |
16 |
The length of the datagram, measured in octets, including Internet header and data. |
Identification |
16 |
An identifying value assigned by the sender to aid in assembling the fragments of a datagram. |
Flags |
3 |
Various control flags. Bit 0: reserved, must be zero Bit 1: (DF) 0 = may fragment, 1 = don't fragment. Bit 2: (MF) 0 = last fragment, 1 = more fragments. |
Fragment Offset |
13 |
Indicates where in the datagram this fragment belongs. The fragment offset is measured in units of 8 octets (64 bits). The first fragment has offset zero. |
Time to Live |
8 |
Indicates the maximum time the datagram is allowed to remain in the Internet system. If this field contains the value zero, then the datagram has to be destroyed. |
Protocol |
8 |
Indicates the next level protocol used in the data portion of the Internet datagram. |
Header Checksum |
16 |
A checksum on the header only. Since some header fields change, such as the time-to-live field, this is recomputed and verified at each point that the Internet header is processed. |
Source Address |
32 |
The source address. |
Destination Address |
32 |
The destination address. |
Options |
variable |
The options may or may not appear in datagrams. A couple of
the available options are: Security: used to carry security, compartmentation, and handling restriction codes compatible with DOD requirements. Record Route: used to trace the route an Internet datagram takes. |
Padding |
variable |
The Internet header padding is used to ensure that the Internet header ends on a 32-bit boundary. The padding is zero. |
Table 3: Description of the Contents in a IP Header
ICMP allows systems on an TCP/IP network to share status and error information. You can use the status information to detect network trouble. ICMP messages are encapsulated within IP datagrams, so they may be routed throughout an internetwork. Two of the most common usages of ICMP messages are ping and tracert.
You can use ping to send ICMP Echo Requests to an IP address and wait for ICMP Echo Responses. Ping reports the time interval between sending the request and receiving the response. Using ping you can determine whether a particular IP system on your network is functioning correctly. There are many different options that can be used with the ping utility. These are covered in depth in Chapter 3.
Tracert traces the path taken to a particular host. It can be very useful when troubleshooting internetworks. Tracert sends ICMP echo requests to an IP address while it increments the time-to-live field in the IP header by a count of one after starting at one and then analyzing the ICMP errors that get returned. Each succeeding echo request should get one further into the network before the time-to-live field reaches 0 and an ICMP Time Exceeded error is returned by the router attempting to forward it.
Exercises 2-1 and 2-2 give you the opportunity to use both the PING and TRACERT utilities.
Exercise 2-1 Ping – to Test Communication with a Distant Computer
Exercise 2-2 Tracert – to Trace the Route Taken to a Distant Computer
The Network Interface layer not only uses the Address Resolution Protocol (ARP) but it is also the location that the Network Driver Interface Specification (NDIS) 4.0 works from.
ARP is used to provide IP address-to-physical address resolution for IP packets. To accomplish this feat, ARP sends out a broadcast message with an ARP request packet in it that contains the IP address of the system it is trying to find. All systems on the local network detect the broadcast message and the system that owns the IP address ARP is looking for replies by sending its physical address to the originating system in an ARP reply packet. The physical/IP address combo is then stored in the ARP cache of the originating system for future use.
All systems maintain an ARP cache that includes their own IP address-to-physical address mapping. The ARP cache is always checked for an IP address-to-physical address mapping before initiating a broadcast.
You can see the contents of your ARP cache by using the ARP utility. There are many different options that can be used with the ARP utility. These are covered in depth in Chapter 3. Exercise 2-3 shows you how to check the contents of your ARP cache.
Exercise 2-3 ARP – To view What Is in the Address Table
Figure 2-8 shows entries in the ARP cache of my system.
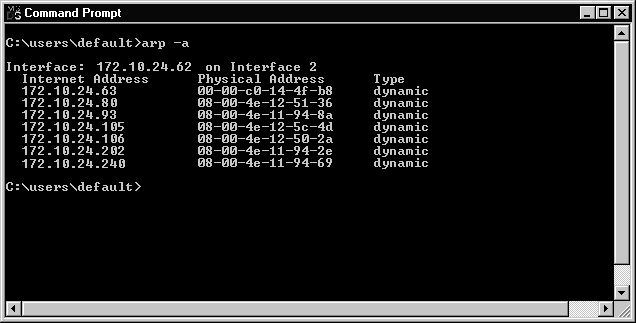
Figure 8: The ARP Cache for a System
NDIS is a standard that allows multiple network adapters and multiple protocols to coexist on the same computer. By providing a standard interface, NDIS permits the high-level protocol components to be independent of the network interface card. All transport drivers call the NDIS interface to access network interface cards.
Figure 2-9 shows a sampling of the protocols available on the four TCP/IP layers.
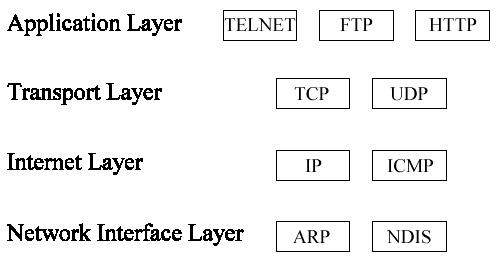
Figure 9: Protocols by TCP/IP Layers
Now that you know about the different protocols used by the TCP/IP layers, here is a quick reference for possible scenario questions, and the appropriate answer:
Begin Q & A
| "Marissa says that it take her "forever" to reach a host in another city…" | Use TRACERT to see the path her machine may be using to contact the other machine. You may be able to isolate a routing problem. |
| "Martha is having a problem with inconsistent data she is receiving from a network application…" | It is possible that the network application uses UDP instead of TCP. Since UDP provides unreliable "best effort" delivery, some data may be lost. You need to see if you can get her an equivalent network application that uses TCP to ensure that all data she needs arrives safely. |
| "James from the sales department tells you that he cannot communicate with a machine in the accounting department…" | You need to run the PING utility to see if the computer is operating correctly on the network. |
In the previous sections, we have seen the layers that make up the OSI and TCP/IP models and the purpose of each of those layers. Now it is time to see what happens as data begins to flow from one layer to the next.
The sending process passes data to the Application layer, which attaches an application header as shown in Figure 2-10.

Figure 10: Data Passed to the Application Layer
The Application layer passes the packet to the Transport layer, which in turn adds its header to the packet as shown in Figure 2-11.
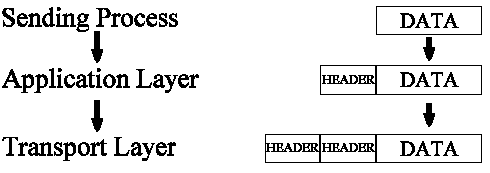
Figure 11: Application Data Passed to the Transport Layer
The Transport layer passes the packet to the Internet layer, which in turn adds its header to the packet as shown in Figure 2-12.
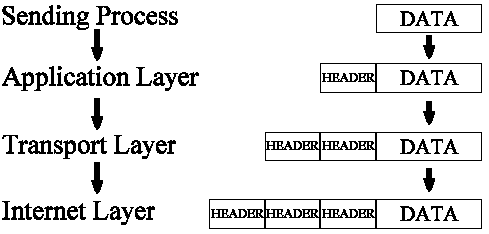
Figure 12: Transport Data Passed to Internet Layer
The Internet layer passes the packet to the Network Interface layer where it is actually transmitted to the receiving computer as shown in Figure 2-13.
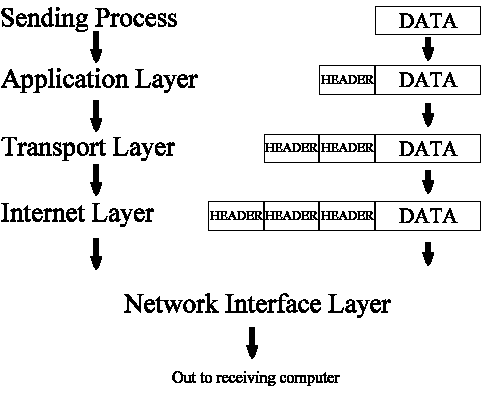
Figure 13: Data Leaving the Network Interface Layer, Headed to the Receiving Computer
On the receiving computer, the different headers are stripped off, one by one, as the packet goes up the layers until it finally reaches the receiving process.
The International Standards Organization developed the Open Systems Interconnect model. The OSI model consists of seven different layers that work as a hiearchy. Each layer can communicate only with the layer directly above or below it. The seven layers of the OSI model are Application, Presentation, Session, Transport, Network, Data Link, and Physical.
Development of the TCP/IP model was funded by the Advanced Research Projects Agency of the Department of Defense. It consists of four different layers that can be equated to the seven layers of the OSI model: Application, Transport, Internet, and Network Interface.
The TCP/IP protocol suite is actually made up of more protocols than just TCP and IP. Some of the other protocols are the Address Resolution Protocol, User Datagram Protocol, File Transfer Protocol, and the HyperText Transfer Protocol. These protocols, as well as others, operate on specific layers of the TCP/IP model.
As data flows from the sending process down the layers of the sending computer, each layer will add its own header prior to handing the packet to the next layer. When the packet starts flowing up the layers at the receiving computer, the headers will get stripped off at each layer until it arrives at the receiving process.
| International Standards Organization (ISO) is responsible for creating, maintaining, and implementing standards for hardware and software. | |
| The OSI model consists of seven layers. | |
| A common mnemonic to help you remember the layers from top to bottom is, "All People Seem To Need Data Processing." | |
| The Application layer is the top layer of the OSI model. It is used to allow applications to access network services. It handles general network access, flow control, and error recovery. | |
| The next layer down is the Presentation layer which is located at layer 6. It is the translator for the network as it determines the format used to exchange data among the computers on the network. | |
| Layer 5 is the Session layer, which establishes a communications connection between processes running on different computers. It performs name recognition and related functions. | |
| Layer 4 is the Transport layer, which is responsible for ensuring that all the data is delivered in the correct sequence, error free, with no losses. It is the Transport layer that breaks up large messages into smaller packets for delivery. | |
| Layer 3, the Network layer, is responsible for determining the route that is taken from the transmitting computer to the receiving computer. It is also responsible for addressing messages and the translation of logical addresses into physical addresses. | |
| Layer 2 is the Data Link layer, which is responsible for providing error-free transfer of frames from one computer to another using the Physical layer. | |
| The Physical layer is located at layer 1, the bottom of the OSI model. The Physical layer handles the unstructured, raw, bit-stream data that is transferred over a physical medium. It also defines how the physical medium, or cable, is attached to the Network Interface Card | |
| Remember the names and functions of each of the seven layers of the OSI model. | |
| The TCP/IP protocol stack is organized into four layers. Each of the four layers of the TCP/IP model exists as an independent module and performs a well-defined function. | |
| The Application layer supports both the NetBIOS interface and the Windows Sockets interface. | |
| NetBIOS over TCP/IP allows NetBIOS client and server applications to be run over the Wide Area Network (WAN). | |
| The Transport layer consists of two protocols, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). | |
| TCP provides a reliable, connection-based delivery service. | |
| UDP offers a connectionless datagram service that is an unreliable "best effort" delivery. | |
| Keep in mind the key differences between the Transmission Control Protocol and User Datagram Protocol. | |
| The Internet layer consists of two protocols, the Internet Protocol (IP) and the Internet Control Message Protocol (ICMP). | |
| IP provides packet delivery for all other protocols within the suite. | |
| ICMP allows systems on an TCP/IP network to share status and error information. | |
| Two of the most common usages of ICMP messages are ping and tracert. | |
| The Network Interface layer not only uses the Address Resolution Protocol (ARP) but it is also the location that the Network Driver Interface Specification (NDIS) 4.0 works from. | |
| ARP is used to provide IP address-to-physical address resolution for IP packets. | |
| NDIS is a standard that allows multiple network adapters and multiple protocols to coexist on the same computer. | |
| Remember the names and functions of each of the four layers of the TCP/IP model. | |
| Remember which layers of the TCP/IP model equate to the layers of the OSI model. | |
| Contained within the four layers of the TCP/IP model are several protocols that direct how computers connect and communicate using TCP/IP. |