| Host Names | |
| HOSTS File | |
| Internetwork Browsing |
A number of network architectures utilize some type of naming system to facilitate the usability and manageability of the network. TCP/IP uses host names, which are simply names assigned to network devices such as servers, workstations, printers, and routers. The host name implementation for TCP/IP is scalable due to its hierarchical structure.
The naming functionality for some other types of networking, such as Novell and Microsoft networks, is less scalable. However, when TCP/IP is used with these networks, they also can benefit from the advantages of its powerful naming system. In fact, each new version of Microsoft and Novell network operating systems relies more on TCP/IP than the previous version. It is likely that future versions of these operating systems will employ only TCP/IP naming in an effort to standardize with the Internet protocols and simplify network administration.
Microsoft networking uses NetBIOS names, commonly called computer names. Although the TCP/IP host name and the NetBIOS name of a Microsoft computer are often the same, they are not required to be identical. Microsoft networks also use browsing, which enables users to easily find other computers by their NetBIOS name on the network. In an internetwork environment, browsing across the entire network requires the use of Windows Internet Name Service (WINS), or carefully designed and managed LMHOSTS files so that computers can find the IP addresses of other computers to participate in browsing.
This chapter will discuss TCP/IP host names, the HOSTS file, and internetwork browsing and the configurations that make it work.
Each device on a given TCP/IP network has a unique IP address, such as 146.115.28.75, and a unique name, such as www.syngress.com. Connections to network hosts on a TCP/IP network can be made by using either the name or the IP address, although using the host name is certainly preferable in most instances.
When connecting to a computer by its host name, the host name must be resolved to an IP address by either one of two ways. Most commonly, the host name is resolved by Domain Name System (DNS), the topic of the next chapter. DNS is a distributed database of host names and IP addresses, and is used on most TCP/IP networks. The second method is by the HOSTS file, a text file on the local computer that contains entries for host names and IP addresses.
Networks that are connected to the Internet must register their domain name with the InterNIC, an organization that sets and maintains standards on the Internet. This ensures that each domain name is unique, which is absolutely necessary for the Internet to function properly.
The administrators of a given domain, on the other hand, must take care to secure unique host names for each device on their network. Since the domain name is guaranteed to be unique by the InterNIC, network administrators do not need to be concerned about the host names on other domains. If the InterNIC and the local administrator have been diligent, each device on the Internet will have a completely unique fully qualified domain name. Table 9-1 summarizes these responsibilities for creating unique names.
| Object | Example | Responsible for Unique Name |
| host name | www | network admin |
| domain name | syngress.com | InterNIC |
| fully qualified domain name | www.syngress.com | InterNIC & network admin |
Table 1 Responsibility for Host and Domain Names on the Internet
TCP/IP domain and host names are subject to certain rules that are necessary to ensure that reliable software and hardware can be developed to handle the various implementation and management details. TCP/IP names, in general, can use alphanumeric characters and the dash (minus sign). Some IP software, including Microsoft's DNS server, also allows the use of the underscore character to support versions of BIND (Berkeley Internet Name Domain) released before version 4.94.
Most TCP/IP utilities can be run using either a local host name, a fully qualified domain name, or an IP address to establish and test network connections with other network hosts. When used with a name, the utility will use either DNS or the HOSTS file to resolve the other host's IP address and then use the IP address to establish communications.
Almost all TCP/IP software includes a Ping utility. Ping is a simple tool that uses the Internet Control Message Protocol (ICMP) to send an echo request to an IP address, as shown in Figure 9-1. When the device that was pinged replies, the Ping program displays information about the replies such as the size and the time it took to reply. Ping needs an IP address to work, so if you ping a host name, it will first resolve the name and then it will go to work carrying out the ping request. If the wrong IP address is returned for the requested name, then the Ping utility will dutifully ping that incorrect address. Always confirm that Ping is using the correct IP address of the device you want to ping.
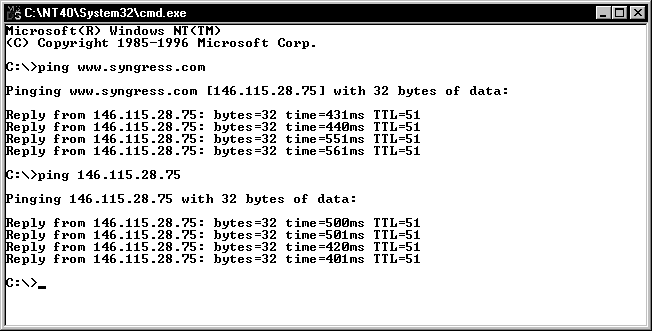
Figure 1 The Ping Utility Can Be Used with Either an IP Address or a Host Name
Some Ping programs will provide additional information such as statistics for the entire ping session. Windows 95 and Windows NT 4.0 do not provide any stats with their Ping utilities, but beta versions of Windows NT 5.0 have an enhanced ping utility that provides extended information that is commonly found on UNIX versions of Ping.
Telnet is a utility used to establish remote command sessions on computers, routers, print servers, and other devices. Like Ping, Telnet can be used with either the host name or the IP address of the remote host. When the host name is used, correct address resolution is required, just as it is for Ping.
Telnet is a heavily used utility with UNIX computers, and is used for everything from e-mail to editing remote files to network administration. Windows NT Server is capable of hosting Telnet sessions as well, and the usefulness of Telnet is becoming appreciated within the Windows NT community. A Telnet server is included with the Windows NT Server Resource Kit, along with another utility, Remote Command Server, that functions somewhat like Telnet but works from the Windows NT command line.
To test the connectivity between two remote computers, an administrator can Telnet to one of the computers, and ping the other computer from within the Telnet session. A Telnet client is included with the TCP/IP connectivity software in both Windows 95 and Windows NT.
File Transfer Protocol (FTP) is a TCP/IP utility that exists solely to copy files from one computer to another. Like Telnet and Ping, FTP can establish a connection to a remote computer using either the host name or IP address, and must resolve host names to IP addresses to establish communication with the remote computer. As you read in Chapter One, Windows NT includes an FTP server in its Internet Information Server software. Windows NT and Windows 95 computers each include a command-line FTP client with their TCP/IP protocol software. Although it is not widely known, the Windows FTP client supports scripting, which enables users to automate repetitive FTP tasks.
There are a number of third-party graphical user interface (GUI) FTP clients for all versions of Windows computers. If you use FTP a lot, a GUI FTP client may save you a lot of time and frustration.
The HOSTS file is a text file that contains IP address to host name mappings. Each HOSTS file entry is entered on a separate line. The format for host entries is to list the IP address followed by one or more spaces, and then the host name. If you wish to add comments, put a pound sign (#) after the host name followed by the comment.
By default, the HOSTS file is located in the %SystemRoot%\System32\Drivers
\Etc directory. Most networks are designed to have client computers use DNS for host name
resolution, so HOSTS files are used sparingly. When DNS is in use, the HOSTS file on a DNS
server is populated with all host name to IP address mappings for the domains it serves.
When adding hosts to the HOSTS file, it is necessary to use the fully qualified domain name of any host that is in a different DNS domain. For hosts that are in the same DNS domain, it is necessary to add only the host name. This rule is necessary so that duplicate names won't appear in the file, while making it unnecessary to use the fully qualified domain name for every host on the local DNS domain. The example in Figure 9-2 shows an entry for a host named "multia" that is in the same DNS domain, and an entry for "www.syngress.com" that is in a different DNS domain.
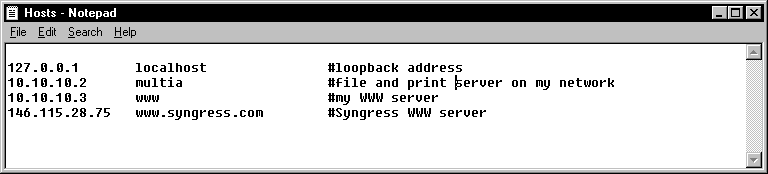
Figure 2 A HOSTS File Containing Entries for Local and Remote Networks
Three steps occur when a host name is resolved using the HOSTS file:
Exercise 9-1 Configuring and Using a HOSTS File
If host name resolution fails, the following items must be checked:
| The HOSTS file does not have an entry for the requested host. | |
| The host name is misspelled in the HOSTS file. This includes capitalization errors since host names are case sensitive. | |
| The IP address for the host entry in the HOSTS file is incorrect. | |
| Multiple entries for a particular host name are listed in the HOSTS file. | |
| A NetBIOS computer name was used in the HOSTS file instead of the TCP/IP host name. |
Users must be able to easily find servers, files, and printers on a network and Microsoft networks implement browsing to accomplish this. Browsing enables a user to "drill down" through the Windows NT domains and servers to find specific files or printers they need. Browsing uses the NetBIOS name of computers, and when used with TCP/IP, this type of communication is known as NetBT (NetBIOS over TCP/IP).
The NetBIOS names inherent with Windows networking are 15-character names with a non-printing character available as the 16th character.
A computer can belong to a Windows NT domain or Windows workgroup, which enables users to browse computers by either of those logical groupings. NetBIOS computer names and Windows NT domain names are not regulated in any way outside of the businesses and organizations that are setting the names for their own networks. This means that uniqueness cannot be guaranteed across disparate entities unless they have collaborated. This is why NetBIOS naming is not an appropriate method of accessing computers on the Internet, and why Windows NT is becoming more DNS-centric with each new version of the operating system.
Microsoft Network browsing is a simple process when it occurs on only one local network and requires no special configuration. When browsing is extended across a TCP/IP internetwork, however, it becomes more complex and it requires specific steps to make it work correctly. WINS or LMHOSTS files must be configured for internetwork browsing to function. When one or both of these components is put in place, the Microsoft browsing service will take care of the details, including the election of domain master, master, and backup browsers. A third alternative that is not recommended is to configure the routers to forward UDP port 137 traffic. UDP port 137 is used by the browser service to carry out its communications on local networks.
Windows NT computers elect among themselves computers, called browsers, to collect and distribute lists of shared resources on the network. Whenever a client browses the network, they request and receive these lists from a browser. There are three types of browsers: 1) domain master browsers; 2) master browsers; and 3) backup browsers. All three are necessary for internetwork browsing and will be automatically elected if either WINS or LMHOSTS is correctly configured. For browsing to work on a local network only, however, the domain master browser is not necessary, and neither WINS nor LMHOSTS need to be configured. Knowing the role that each browser plays is essential to understanding how internetwork browsing works. The distinction between local network browsing and internetwork browsing is summarized in Table 9-2.
Browsing uses computer NetBIOS names, not DNS names, so whenever "names" and "browsing" are mentioned together, it is safe to assume that the reference is to a NetBIOS name. Browsing requires special designations, such as domain master, browser, and master browser, to be associated with computer names. DNS currently does not have the capability to fulfill this requirement so it cannot be used to implement internetwork browsing.
| Local Network | Internetwork |
| Master Browser | Domain Master Browser |
| Backup Browsers | Master Browsers |
| Backup Browsers | |
| WINS, LMHOSTS, or Routers Configured to Forward UDP Port 137 |
Table 2 Browsing Components Necessary for Local and Internetwork Browsing
Computers that have been configured specifically not to become a master or backup browser are called non-browsers. Configuring most client PCs to be non-browsers will reduce the possibility of having browsing problems. To configure a computer to be a non-browser, the registry setting MaintainServerList is set to "no" (see Table 9-3).
A potential browser is a computer that can become a master or backup browser. In order for it to become a backup browser, the master browser must designate it as such. If there is no master browser, a potential browser will force an election.
A master browser is responsible for collecting information about the servers in its workgroup or the servers in its domain that are on the same subnet. When a server is started, it announces itself to the master browser with a directed datagram called a server announcement. Windows NT Server, Windows NT Workstation, Windows for Workgroups, Windows 95, and LAN Manager servers all send server announcements at startup. If a domain spans more than one subnet, the master browser will maintain the resource list only for the portion of the domain on its subnet. Master browsers also send resource lists to backup browsers and provide lists of backup browsers to clients.
| Value | Description |
| No | This computer will not be a browser. |
| Yes | This computer will be a master or backup browser. This is the default setting for Windows NT Server. |
| Auto | This computer will become a browser if needed. This is the default setting for Windows NT Workstation. |
Table 3 Values for \HKEY_LOCAL_MACHINE\System\CurrentControlSet\
Services\Browser\Parameters, MaintainServerList
A domain master browser receives lists of resources from each master browser in the internetwork, which enables it to compile a list of all resources available on the internetwork. This complete list is then distributed back to the master browsers. The domain master browser is always a primary domain controller (PDC), and is very likely to be the master browser of its own subnet.
The master browsers announce themselves to the domain master browser with a MasterBrowserAnnouncement directed datagram. The domain master browser then issues a remote NetServerEnum API call to each master browser about which it knows. This is a request for the master browser to send the resource list that it is maintaining. By default, this call is repeated every 15 minutes, making sure that the resource lists are reasonably current. The domain master browser thus collects the browser list from each master browser on the internetwork and compiles the complete list of resources available.
Each master browser in turn issues the NetServerEnum request to the domain master browser, collecting the entire list of resources on the internetwork. As this information is then distributed to backup browsers, clients are able to browse the entire internetwork.
A backup browser receives the resource list from the master browser and fulfills browse requests from the clients in its domain or workgroup. If a Windows NT domain controller is not a master browser, it will automatically become a backup browser. If there are not enough Windows NT Server computers to fill the needed backup browser roles, Windows NT Workstation, Windows for Workgroups, and Windows 95 computers can perform the duties of backup browser.
Backup browsers contact the master browser every 15 minutes to get the latest list of resources. Whenever a client sends a NetServerEnum request to a backup browser, the backup browser forwards the list of resources to the client. If a backup browser cannot find the master browser, it forces an election, and a new master browser is designated.
The number of backup browsers that exist for a given domain or network segment depends on the number of computers in the domain or segment, as shown in Table 9-4. In some instances, these numbers will vary since BDCs are automatically backup browsers. For example, if a network with fewer than 31 computers has two BDCs, there will be two backup browsers instead of just one. The standards in Table 9-4 can also be broken if the MaintainServerList registry entry is manually set to "yes" on computers.
| Computers | Backup Browsers |
| 1 | 0 |
| 2 - 31 | 1 |
| 32 - 63 | 2 |
| 63+ | +1 for each additional 32 computers |
Table 4 The Number of Backup Browsers Designated Depends on the Number of Computers in the Domain or on the Network Segment.
A browser election is a process to determine which computer will be the master browser. There are four circumstances that will force a browser election to take place:
| A client or backup browser cannot find a master browser. | |
| A server with MaintainServerList set to "yes" is started. | |
| A Windows NT primary or backup domain controller is started. | |
| A Windows NT computer with IsDomainMasterBrowser set to "yes" is started. |
When any of these situations arises, the computer initiating the election sends out an election datagram. All browsers receive this datagram and examine its election criteria. If the receiving computer's election criteria are better than the sender's criteria, the receiver enters into an election-in-progress state and issues its own election datagram. Otherwise, it will try to determine which computer is the new master browser. A number of criteria, listed in Table 9-5, are used to determine which computer wins the browser election.
| Election Datagram | Description |
0xFF000000 |
Type of Operating System |
0x01000000 |
Windows for Workgroups/Windows 95 |
0x10000000 |
Windows NT Workstation |
0x20000000 |
Windows NT Server |
0x00FFFF00 |
Election Version |
0x000000FF |
Criteria Per Version |
0x00000080 |
Primary Domain Controller |
0x00000020 |
WINS Client |
0x00000008 |
Preferred Master Browser |
0x00000004 |
Currently a Master Browser |
0x00000002 |
MaintainServerList Set to Yes |
0x00000001 |
Currently a Backup Browser |
Table 5 The Master Browser Is Elected after Comparing Each Browser's Election Criteria.
For example, the election datagram of a Windows NT Server computer that has been configured as a preferred master browser will be 0x00000008. A computer that is currently a backup browser will receive this datagram and notice that its own election criteria are better. Therefore, it will send out its own election datagram and enter into the election-in-progress state.
As you may have realized, there is likely to be more than one backup browser on the network, and there must be some way to "break the tie" since the backup browser criteria is the highest election criteria specified. In this case, two rules will be followed to select the new master browser: 1) the browser that has been running the longest will win, and then 2) the browser with the lowest name alphabetically will win. The chances of an election being decided by the alphabetical criteria are miniscule.
After a browser has determined that it has won the browser election, it enters into the running election state. During this time it sends out an election request after a short pause. The length of the delay depends on the browser's role:
| Primary domain controllers and master browsers pause for 100 microseconds. | |
| Backup domain controllers and backup browsers delay for 600 and 200 microseconds. | |
| Other browsers delay between 800 and 3000 microseconds randomly. |
This delay is implemented so that browsers that are less likely to win elections won't end up sending election datagrams. This reduces network traffic and the number of election packets that must be analyzed by each browser. The pause also keeps browsers from actually becoming the master browser before all of the other browsers have had time to broadcast their election criteria.
A browser sends up to four election datagrams, and is promoted to master browser if no greater election criteria are received from other computers. If it is currently the master browser and receives better criteria from another browser, it will demote itself to backup browser. Events are recorded in the Event Viewer's System log on a Windows NT computer when it forces an election, including separate events for each protocol on which the browser service forces the election.
Now that you understand how browsing works, we will take a look at how browsing operates in a WAN environment. On a given TCP/IP network segment, the browsing service uses UDP port 137, which will not be forwarded by routers unless they are specifically configured to do so. Having routers forward browser traffic on large WANs will likely cause some problems, including much too frequent browser elections.
The browsers on each segment will elect a master browser for that segment. This master browser will assign backup browser duties to an appropriate number of computers. The master browser will also send a MasterBrowserAnnouncement datagram to the domain master browser. The election process is illustrated in Figure 9-3. The domain master browser will usually be across a router, which is why WINS or LMHOSTS must be in place for TCP/IP WAN browsing to function–or less desirably, UDP port 137 datagrams must be forwarded by the routers.
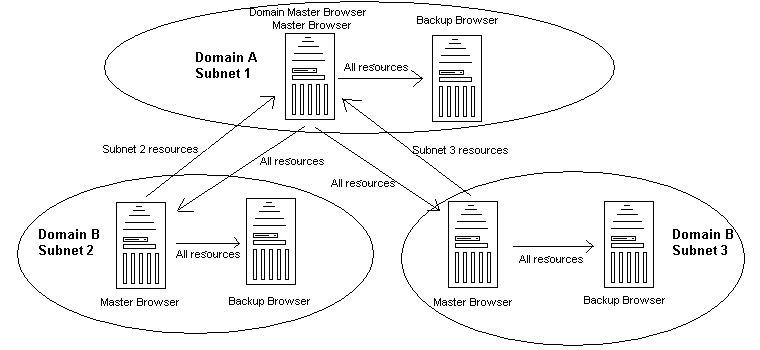
Figure 3 The Master Browser of Each Subnet Sends Its Resource List to the Domain Master Browser, and in Turn Receives a List of All Internetwork Resources from the Domain Master Browser.
Microsoft recommends that TCP/IP WAN networks implement WINS, which was discussed in the previous chapter. Deploying WINS is the preferred way to accomplish WAN browsing since it requires less manual configuration, automatically adjusts to reflect changes in the network resources, and is less susceptible to human error.
Computers that are serving as browsers will register special names, shown in Table 9-6, with the WINS service that will identify them as potential browsers, master browsers, and domain master browsers. The 16th byte is used to designate the type of browser the computer is.
Once WINS is in place, the browser service will use it without any special configuration. WINS enables master browsers to determine which computer is the domain master browser, even though it may be on different network segment. It also enables the domain master browser to easily locate all browsers and potential browsers. Client computers must be WINS-enabled as well for them to be able to browse the internetwork A client can then locate the master browser for its domain by querying the WINS server.
| Registered Name | Description |
| \\<domain_name>[1B] | This name is registered by the Windows NT system that is the domain master browser, and allows remote browsing of domains. A WINS Server returns the IP address of the system that registered this name when a client queries for this name. |
| \\--__MSBROWSE__[01] | This name is registered by the master browser and is used to broadcast and receive domain announcements on the local subnet. It is through this name that master browsers for different domains learn the names of different domains and the names of the master browsers on those domains. When a WINS Server receives a name query for this name, the WINS Server will always return the subnet broadcast address for the requesting client's local subnet. |
| \\<domain_name>[1E] | All browser and potential browsers in a domain or workgroup register this name. Master browsers use these entries for announcement requests in order to fill up its browse lists and for election requests. |
Table 6 Special Browser Entries Registered in WINS- Enable Browsers and Clients to Find Browsers on Other Subnets.
Another way that computers can find each other based on NetBIOS names in an internetwork is to configure the LMHOSTS file for each computer. This is similar to the HOSTS file, except it is for NetBIOS names instead of TCP/IP names.
The LMHOSTS file is a text file located by default in the \<winnt_root>\System32\drivers\etc directory. A sample file, LMHOSTS.SAM, is installed whenever TCP/IP is installed on a Windows NT computer. For internetwork browsing to function using LMHOSTS, there are a number of LMHOSTS entries that need to be present:
| The NetBIOS names and IP addresses of all browsers must be listed in the LMHOSTS file of the domain master browser. | |
| The PDC for each domain must be entered with the #DOM tag into the LMHOSTS file on each master browser. | |
| Each master browser's LMHOSTS file must have an entry for the domain master browser, including the #PRE and #DOM extensions. |
As you can see, using this method to enable WAN browsing requires a great deal of manual configuration, and must be updated whenever a domain or network segment is added or removed. The #INCLUDE function in the LMHOSTS file can alleviate most of the work, but you will still have to manually maintain a central LMHOSTS file.
Exercise 9-2 Browsing with LMHOSTS File
The NetBT Name Service uses UDP port 137, as defined in RFCs 1001 and 1002. Routers typically filter this traffic because it is used for hardware and subnet broadcasting. Some routers are capable of being configured to forward UDP port 137, and doing so will allow browsing to function without the use of WINS or LMHOSTS. This method is not recommended for a number of reasons.
| Browser elections will not function correctly if computers across slow links cannot respond in a timely manner. | |
| Browser elections will involve a greater number of computers, thus generating more browser traffic that will hit every segment of the WAN. | |
| Browsing will be slower since computers will have to communicate across routers to supply resource lists to clients. |
Two utilities come with the Windows NT Server Resource Kit that enable you to view browser information, force elections, and stop master browsers. These utilities will be invaluable if you have trouble with internetwork browsing.
Browmon.exe is a GUI tool that allows you to see the master and backup browsers for specified domains. If more than one transport protocol is in use, the browsers for each protocol will be listed. Browmon also provides statistics about the number of server announcements, domain announcements, election packets, and other information.
Browstat.exe is a command-line utility that gives you the ability to force elections and stop master browsers, which also forces an election. Documentation for these two tools is included in the Resource Kit books and Help files.
In order for users and applications to make use of TCP/IP host names, the host names must be resolved to IP addresses. This can be accomplished by either DNS or the local HOSTS file. The HOSTS file is a text file containing entries that associate IP addresses with host names. When supplied with a host name, the computer parses its HOSTS file and returns that host’s IP address to the application. HOSTS files are not used on most client PCs since DNS is a more manageable solution for host name resolution.
Microsoft networking uses NetBIOS name browsing to enable users to easily find files and printers located on other computers. The resource lists for a network are gathered and distributed by three types of browser computers: master browsers, backup browsers, and domain master browsers.
Since browsing uses UDP port 137, which by default is not forwarded by routers, you must configure the network in one of three ways to enable internetwork browsing. The best way to implement internetwork browsing is to use WINS servers. Browsers register their names with specific 16th byte characters identifying their browsing role. This enables the domain master browser to find all of the master browsers on an internetwork to coordinate the collection and distribution of resource lists.
The second way to make internetwork browsing function is to configure the LMHOSTS files on all browser computers with the appropriate entries. This is a manual process, subject to human error.
The third and least recommended way is to configure the routers on the network to forward UDP port 137 traffic. This will cause more network traffic on each segment of the network and may cause problems with browser elections if low-speed WAN links are in use. This method would be considered in only the smallest routed network environments.
| Each device on a given TCP/IP network has a unique IP address, such as 146.115.28.75, and a unique name, such as www.syngress.com. | |
| When connecting to a computer by its host name, the host name must be resolved to an IP address by either one of two ways. | |
| The host name is resolved by Domain Name System (DNS) or by the HOSTS file, a text file on the local computer that contains entries for host names and IP addresses. | |
| Networks that are connected to the Internet must register their domain name with the InterNIC. | |
| Most TCP/IP utilities can be run using either a local host name, a fully qualified domain name, or an IP address to establish and test network connections with other network hosts. | |
| Ping is a simple tool that uses the Internet Control Message Protocol (ICMP) to send an echo request to an IP address. | |
| Telnet is a utility used to establish remote command sessions on computers, routers, print servers, and other devices. | |
| File Transfer Protocol (FTP) is a TCP/IP utility that exists solely to copy files from one computer to another. | |
| The HOSTS file is a text file that contains IP address to host name mappings. | |
| When adding hosts to the HOSTS file, it is necessary to use the fully qualified domain name of any host that is in a different DNS domain. | |
| Users must be able to easily find servers, files, and printers on a network and Microsoft networks implement browsing to accomplish this. | |
| Browsing enables a user to "drill down" through the Windows NT domains and servers to find specific files or printers they need. | |
| There are three types of browsers: 1) domain master browsers; 2) master browsers; and 3) backup browsers. | |
| Computers that have been configured specifically not to become a master or backup browser are called non-browsers. | |
| A potential browser is a computer that can become a master or backup browser. | |
| A master browser is responsible for collecting information about the servers in its workgroup or the servers in its domain that are on the same subnet. | |
| A domain master browser receives lists of resources from each master browser in the internetwork, which enables it to compile a list of all resources available on the internetwork. | |
| A backup browser receives the resource list from the master browser and fulfills browse requests from the clients in its domain or workgroup. | |
| A browser election is a process to determine which computer will be the master browser. | |
| Microsoft recommends that TCP/IP WAN networks implement WINS. | |
| Be sure you understand the three types of browsers, how to configure browser registry entries and the three methods of implementing internetwork browsing. | |
| Another way that computers can find each other based on NetBIOS names in an internetwork is to configure the LMHOSTS file for each computer. | |
| Two utilities come with the Windows NT Server Resource Kit that enable you to view browser information, force elections, and stop master browsers. |