Chapter 7
*Understanding Windows NT Networking
*From the Classroom *
Protocols *
Interprocess Communication (IPC) *
Network Settings
*Managing Shared Directories
*Browsing the Network *
Certification Summary
*Two-Minute Drill
*Self Test
*
Chapter 7
Understanding Windows NT Networking
![]()
| NT’s Networking Model | |
| NetBEUI, NWLink, TCP/IP, DLC | |
| Redirectors and IPC | |
| Managing Shared Resources on the Network |
NT is known for its networking capabilities. It has built-in networking capabilities that allow it to operate in a heterogeneous network environment. Heterogeneous means a mixed network operating environment involving different operating systems like NT, UNIX, and Novell. NT uses a layered networking model, which makes it easier to write network applications and hardware drivers. The NDIS layer allows multiple protocols to bind to a single network adapter. NT has grown in popularity because of its ability to connect to so many different systems. It comes with a Microsoft redirector and a Microsoft-developed Novell redirector, allowing it to connect to NT, LAN Manager, LAN Server, NetWare, and any SMB-compliant network operating system. NT also supports many open system architectures like UNIX and Open VMS.
NT is an operating system (OS) and a networked operating system (NOS). Years ago, the OS and the NOS were two separate software components. Your computer's OS was probably MS-DOS and your NOS was probably Novell. NT bridges the gap between the OS and the NOS by providing built-in networking.
NT uses several components to provide a robust NOS, capable of operating in a heterogeneous network. Redirectors are used to access other computers on the network, and server services provide other computers on the network access to your workstation. NT supports several protocols out-of-the-box, and has room to support more. NT uses an interprocess communication (IPC) to communicate with other computers. NT supports six different IPC mechanisms that we'll discuss later.
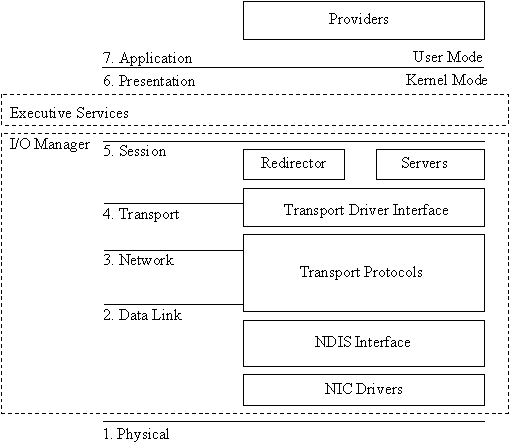
Figure 1: The NT networking model corresponds to the OSI networking model.
NT Networking Model
The NT networking model is made up of layers, which loosely correspond to the seven layers of the OSI networking model. Figure 7-1 shows the NT networking model and how it corresponds to the OSI model.
Each layer can talk only with the layers directly above and below it. The MAC sublayer is where the network interface card (NIC) driver resides, and this is where the model begins. The driver is responsible for linking the NIC to the network. The NDIS interface layer is the next layer. The NDIS interface layer is a special layer that allows hardware vendors to write NIC drivers that access the NDIS layer, regardless of which transport protocols are used. NDIS allows multiple NICs to bind to multiple protocols without requiring a separate protocol stack for each card. The third layer, transport protocols, defines how data should be presented to the next receiving layer, and packages that data accordingly. The fourth layer serves a similar purpose as the NDIS layer. The transport driver interface (TDI) allows redirectors to be written without concern for the transport protocol being used. The fifth layer provides for the redirector. The redirector redirects local requests for shared network resources to the appropriate network share.
In order to access other computers and shared resources on the network, you must have a way to get out to the network. NT uses redirectors to give client computers access to server services. Now that you're on the network, it only makes sense that there must be some shared resource that you need to access. The server service enables other computers to connect to shared resources on your system. The redirector lets you out, and the server lets others in to your computer. Actually the redirector is one part of the workstation service.
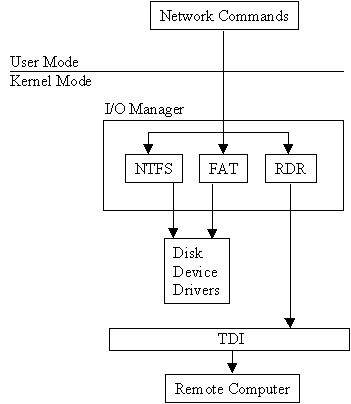
All user mode requests pass through the workstation service. The workstation service is made up of two parts:
| User mode interface, which resides in the services.exe | |
| The redirector (rdr.sys), which is a file system driver that interacts with the lower-level NIC drivers by means of the TDI |
Figure 7-2 depicts the workstation service receiving a request and passing it to the redirector.
Figure 2: The Workstation service receives a request and passes it to the redirector.
Windows NT Redirector
As previously mentioned, the redirector is implemented as a file system driver. Implementing the redirector as a file system has many advantages.
| It runs in Kernel mode, allowing it to call other drivers and Kernel mode components. | |
| It can load and unload dynamically. | |
| It can coexist with other redirectors. | |
| It allows applications to access files on a local and remote computer by calling a single API. The NT I/O Manager doesn't distinguish between accessing files locally or remotely. |
Providers and the Provider-interface Layer
Each additional type of network must have a provider installed (Banyan Vines or NetWare). The provider allows NT to communicate with the network. NT Workstation comes with a provider, Client Services for NetWare. This allows NT Workstation to access resources on a Novell NetWare server.
The server service allows remote computers to connect to NT Workstation. The redirector sends client computers to your workstation, where the server service provides them with requested resources. The following steps, illustrated in Figure 7-3, occur when the server service receives a request from a client workstation to read a file:
- The low-level network drivers receive the request and pass it to the server driver.
- The server passes a read file request to the proper local file system driver.
- The local file system driver calls a lower-level disk driver to access the file.
- The data is sent back to the local file system driver.
- The local file system driver sends the data back to the server.
- The server passes the data back down to the low-level network drivers so it can be transmitted back to the client workstation.
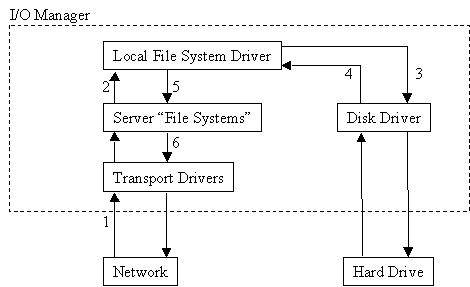
Figure 3: The server service receives a request from a client workstation.
NT Workstation on the Network or How to turn your network upside down without really trying
A big surprise to many of our students is that, when you install NT Workstation, it automatically installs and starts the server service. This can be a nasty surprise when you are installing Workstation back in your organization.
We were doing some wide area network design at a client’s site, and it came to the client’s attention that we also had a great deal of expertise in NT and NT networks. The client had recently installed 3,800 computers, all with NT Workstation. The client had set up several domains, and had the NT Workstations in various workgroups. Some of the workgroups contained only a single NT Workstation, several others contained a couple of workstations, while a number of workgroups contained 75 or 80 computers. This design is pretty funny. Well, it’s funny to a serious NT person, anyway!
There are many problematic issues with the layout of this network. One of the more significant issues is the deployment of NT Workstation with the default installation that installs and starts the server service. With the server service running, NT Workstation is a server on the network. This means that each of the Workstations is sending browser registration traffic and browser announcements.
Our client did not understand the disadvantage to having the server service enabled. To illustrate the point, we asked what he would think if he had a network of 3,800 NetWare servers. He replied that the network would be unmanageable. I think he got the point.
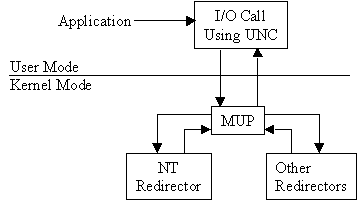
The MUP handles I/O requests containing UNCs. When an application makes an I/O call using a UNC, the MUP selects the appropriate redirector to handle the request. When a request is received containing a UNC, the MUP checks with each redirector to find out which one should process the request. The redirector with the highest-registered response is used to establish the connection. The connection remains as long as there is activity over the connection. If there is no activity for 15 minutes the MUP renegotiates to find an appropriate redirector. Figure 7-4 depicts where the MUP is logically located.
Figure 4: The MUP selects the appropriate redirector to handle a request.
Applications that don't use UNC names in their I/O requests use a different method to select a redirector. MPR receives WNet commands (part of the Win32 network APIs), chooses the proper redirector, and passes the command to the selected redirector. Since different vendors use different interfaces for communicating with their redirector, there is a series of provider DLLs between MPR and the redirectors. Figure 7-5 illustrates the MPR’s function.
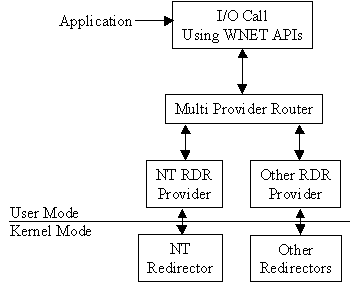
Figure 5: MPR passes WNet commands to the selected redirector.
Protocols are languages used by computers. In order for two computers to talk to each other they must speak the same language (use the same protocol). Why doesn't everyone just accept a standard protocol? That’s just like asking why everyone doesn’t speak the same language. Could the world tell everyone in America that they are going to have to learn French because that's the new world standard? The same is true with computer companies developing networked computer systems. Novell developed IPX/SPX, and it's partial to its own creation. Microsoft used to be tied to NetBEUI, but now has adopted TCP/IP as its standard protocol. TCP/IP is a pseudo-standard. The Internet uses TCP/IP and, since the Internet is growing at an exponential pace, TCP/IP is growing just as fast.
NetBEUI is a fast, small, and non-routable protocol. It's used mainly for backward compatibility to Microsoft's LAN Manager and IBM's LAN Server network operating systems. It's easy to install because no configuration is required. You should use NetBEUI if you have a few computers networked, with no routing between subnets. Since NetBEUI isn't routable, it can't be used with the Internet, which is why it has lost popularity.
NWLink is Microsoft's implementation of Novell's IPX/SPX protocol. Since Novell owns the copyright on IPX/SPX, Microsoft had to reverse engineer the protocol. NWLink is a fast and routable protocol that doesn't require configuration. It's used primarily to communicate with Novell servers. NWLink by itself won't access a Novell server; it needs a redirector to access the Novell server.
Transmission control protocol/Internet protocol (TCP/IP) is the default protocol for Windows NT. The Internet uses TCP/IP; therefore, TCP/IP is considered a global standard. TCP/IP is a bigger protocol than NetBEUI and NWLink, and it requires configuration. Although TCP/IP requires configuration, you can use DHCP to configure your workstation. NT Server can be used as a DHCP server to provide the TCP/IP configuration. TCP/IP is the default protocol installed when you enable networking in NT.
Data Link Control (DLC) is not a computer-to-computer protocol. It's used as a gateway protocol. SNA server uses DLC to communicate with IBM mainframes. DLC is also used for printing to network printing devices equipped with the DLC protocol. Computers communicate with the gateway server using NetBEUI, NWLink, or TCP/IP. Then the server uses DLC to communicate with the requested device.
AppleTalk Filing Protocol (AFP) ships with NT as a development tool for developers who write Macinitosh applications under NT. AFP is used on NT Server to support Services for Macintosh, but it’s also possible to use NT Workstation to develop AFP applications.
Interprocess Communication (IPC)
Interprocess communications (IPC) is the process of exchanging data or instructions between two computers. IPCs support two-way communications between computers. NT supplies six methods of IPC: NetBIOS, Windows Sockets, named pipes, mailslots, NetDDE, and remote procedure calls (RPC).
The Network Basic Input/Output System (NetBIOS) is a session-level interface used by applications to communicate with NetBIOS-compliant transport protocols. NetBIOS has been around since the early 1980s. Since NetBIOS has been around so long, it is now used mainly for backwards compatibility to older systems.
The NetBIOS interface is responsible for: establishing logical network names, beginning sessions between two computers, and supporting reliable data transfer between computers that have an established session. The logical network name is used to uniquely identify each computer on the network. The name is made up of 1 – 15 characters. One of the drawbacks to NetBIOS naming is that it is a flat namespace. You'll need to be careful when planning a naming convention for your network. If you use last names for computer names, you'll quickly run into problems, especially if you manage a large network, or if your network grows beyond your planned size. After a session is established, computers can communicate in the form of NetBIOS requests or in the form of Server Message Block (SMB). NetBIOS can be implemented over TCP/IP, NWLink, or NetBEUI. A NetBIOS client-server application can communicate over various protocols: NetBEUI protocol (NBF), NWLink NetBIOS (NWNBLink), and NetBIOS over TCP/IP (NetBT).
Windows Sockets (Winsock) is the windows implementation of the UC Berkeley Sockets API. Microsoft TCP/IP, NWLink, and AFP use this interface. A socket provides an endpoint to a connection. Two sockets make a complete path. The two sockets work as a bi-directional pipe for incoming and outgoing data between two computers.
Named pipes provide connection-oriented communications. This means they guarantee delivery of the data. Named pipes help client-server applications by providing a secure channel between two processes for exchanging data. Named pipes also provide for impersonation. This allows the server to process the client request in the security context of the client. Using impersonation ensures that the client's process doesn't exceed his level of permissions.
Mailslots provide connectionless communications. This means they do not guarantee delivery of data. Mailslots are generally used for broadcast messages. The browser service uses mailslots to advertise your arrival on the network.
Remote procedure calls (RPC) are the most flexible and robust of the IPC mechanisms. RPC uses other IPC mechanisms to establish communications between two computers. RPC can ride over named pipes, NetBIOS, or winsocks to communicate with other computers. An RPC can be established on the same computer as a client call to a server. It does this by using the local procedure call (LPC) to transfer information between processes and subsystems.
Network dynamic data exchange (NetDDE) allows two applications to communicate, with a link always maintained. The link must always be maintained so that when the server registers a change, all other clients receive the message of the change. MS Hearts and Chat are two examples of NetDDE.
The NetDDE IPC by default is not started. Whenever you start a NetDDE-enabled application, the NetDDE IPC automatically starts. NetDDE depends on a hidden share called NDDE$. This share maps to a DDE process, not a folder. The share is created whenever a NetDDE-enabled application is started. NetDDE provides information-sharing capabilities by opening two one-way pipes between applications.
In this section I'll take you through opening the Control Panel, adding a service, removing and reinstalling a service, installing a transport protocol, and changing the domain that your workstation participates in.
Exercise 7-1 Opening the Network Control Panel
Or
- Click Start | Settings | Control Panel.
- Double-click the Network icon.
In exercise 7-2 we'll add Simple TCP/IP Services to your NT Workstation.
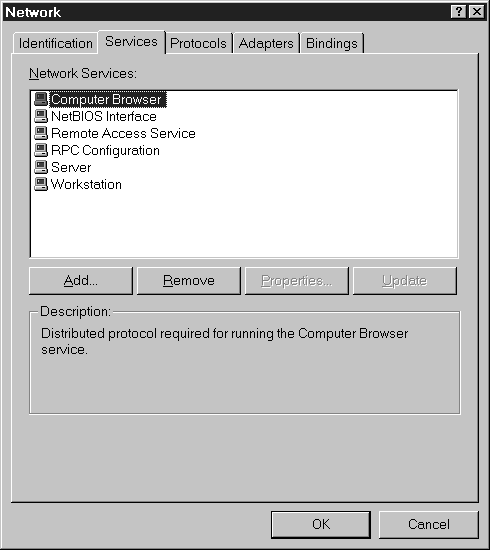
Figure 6: The Network properties Services tab.
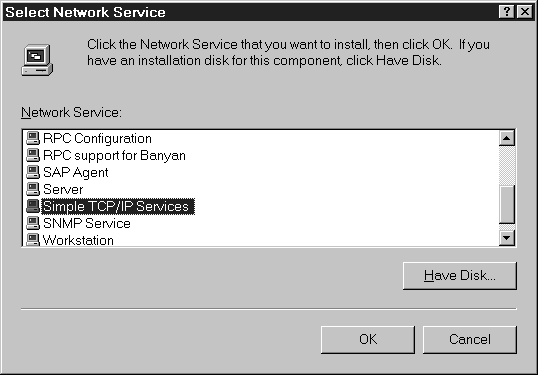
Figure 7: Adding a network service.
The next exercise teaches you how to remove a service, and then reinstall that same service. This is a necessary procedure when you think a service has a corrupted DLL file and you wish to fix it. Remember that, after installing new services or components to NT, you need to reinstall your latest NT service pack. The key to this exercise is step 5. After removing a service, you must restart your computer before adding that service back.
Exercise 7-3 Removing/Reinstalling a Removed Component
Exercise 7-4 shows you how to add NetBEUI as a protocol to your system.
Exercise 7-4 Installing a Transport Protocol
The next exercise teaches you how to remove your computer from a workgroup and add it to a domain. For this exercise you'll need an NT server on your network configured as a domain controller. You'll also need to have administrative rights to the domain.
Exercise 7-5 Changing the Domain or Workgroup
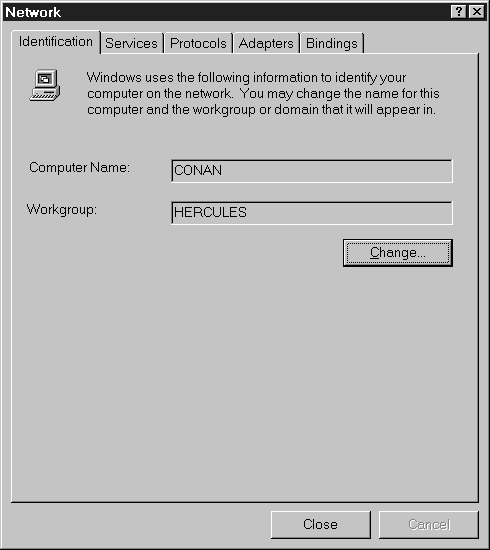
Figure 8: The Identification tab in Network Properties.
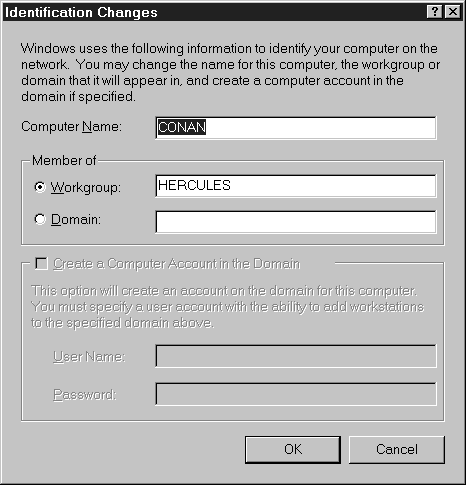
Figure 9: Changing the Workgroup to a Domain.
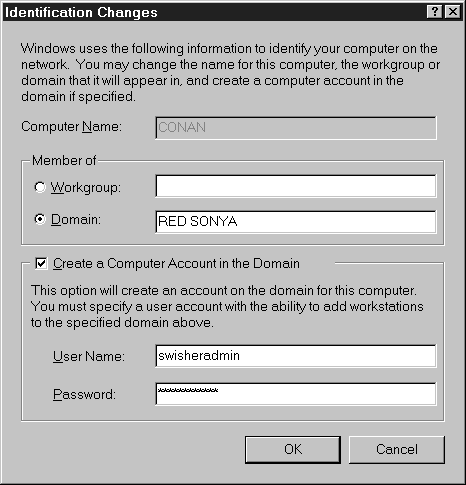
Figure 10: Adding a computer account on the domain.
The Bindings tab in Network Control Panel allows you to set the order in which protocols, adapters, and services are processed. Binding is the linking of network components on different levels to enable communication between those components. A network component can be bound to one or more network components above or below it. The services that each component provides can be shared by all the components bound to it. The higher an object is in the order, the faster it's accessed. You also can disable an adapter, a protocol, or a service at the Bindings tab. Figure 7-11 shows the Network Control Panel bindings tab.
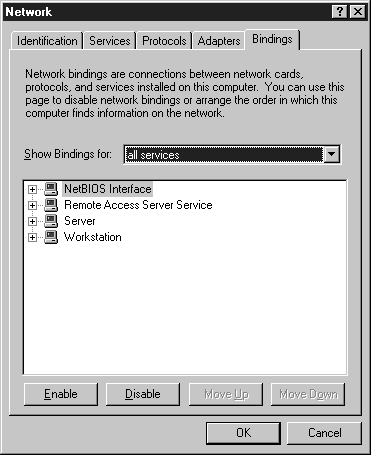
Figure 11: At the Bindings Tab you can set the order in which protocols, adapters, and services are processed.
You can view all services, all protocols, or all adapters by using the drop-down menu Show Bindings For. By clicking the + signs, you can expand the branches. Figure7-12 shows all adapters bindings expanded out for adapter [3].
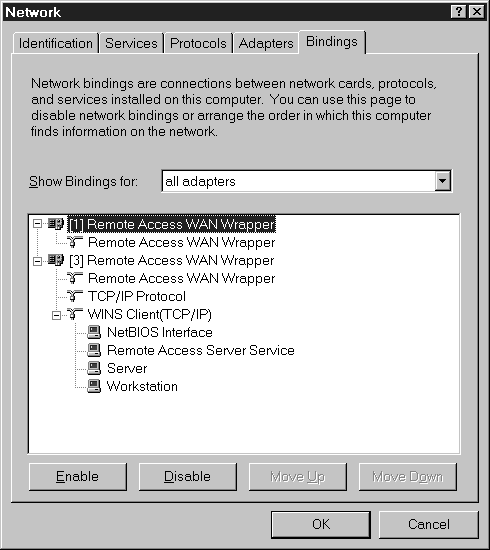
Figure 12: Bindings tab showing all adapters expanded out for adapter [3].
In exercise 7-6 you go through the steps of changing the priority of the transport protocol. For this exercise you'll need at least two protocols installed on your workstation. This exercise assumes that you have TCP/IP and NetBEUI installed, and that NetBEUI is higher in the binding order before we start the exercise. Since all of our servers have TCP/IP as their default protocol, we want to make TCP/IP higher in the binding order.
Exercise 7-6 Changing the Priority of Transport Protocols
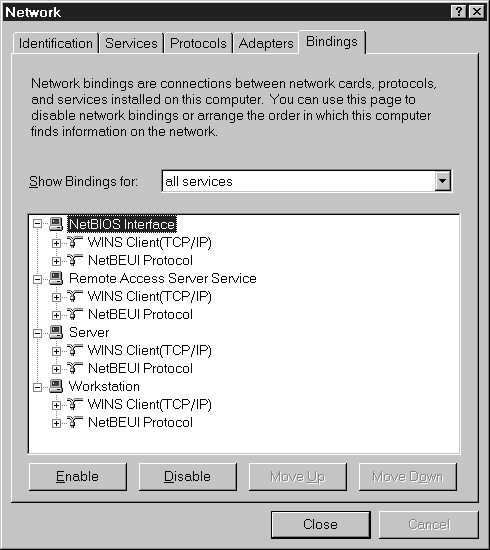
Figure 13: NetBEUI is higher in the binding order.

Figure 14: TCP/IP is higher in the binding order.
Once a share is created, the best way to manage the share is through the Server applet in Control Panel. Using the Server applet you can monitor the following:
| Total number of active sessions | |
| Total number of open files currently accessed via the network | |
| Total number of file locks placed by remote users against the open files | |
| Total number of open named pipes between your workstation and remote clients |
The Server applet allows you to enter a description of your computer that shows up in server manager. You can do more than just look at the open connections; you also can manage the connections using the control buttons located at the bottom of the Server applet.
There are five buttons on the Server applet, but we'll discuss only the first three: Users, Shares, and In Use.
The Users button opens the User Sessions dialog box. The User Sessions dialog box allows you to view a list of all the network users connected to the computer, and list all the resources opened by a selected user. Optionally, you can disconnect one or all of the users connected to the computer.
The Shares button opens the Shared Resources dialog box. Use this dialog box to view a list of the shared resources available on the computer and, for a selected resource, a list of connected users. Optionally, you can disconnect one or all of the users connected to the computer.
The In Use button opens Open Resources dialog box. Use this dialog box to view a list of the computer's open shared resources. You also can close one open resource, or all open resources.
NT creates hidden shares for administrative purposes. Two hidden administrative shares are the C$ and the Admin$. Only administrators can access both these shares. Backup Operators can access the C$. This is necessary so that they can backup all files on hard disks. The $ symbol at the end of a share makes it hidden. When users browse your computer for shared resources, shares that end with $ won't be seen. Users can still connect to hidden shares, but they must know the name of the share and have the proper permissions. You can map a drive or use a UNC to connect to a hidden share.
You can stop these shares, but they will be recreated the next time the computer restarts. However, you can use the Windows NT system policy editor to edit the Registry to always have these shares removed.
This administrative share shares the root system root directory, regardless of which folder it was created in. This allows administrators easy access to the operating system folder on any NT computer.
The C$ is created to allow administrators to the computers drive C: root directory. Administrators can quickly map a drive to a user's C$ to access files and folders. If the system has more than one partition, a similar share is created for each partition (D$, E$, and so on). CD-ROMs and floppy drives don't automatically create hidden administrative shares.
The Computer Browser is a service that allows your computer to be seen on the network. The Computer Browser service maintains a list of available servers on the network and provides that list to the clients when requested. A server is any computer that provides server services, so Windows95 and Windows 3.11 are also considered servers if they have file and print sharing services enabled. Every workgroup on every subnet has a master browser. Domains also have a master browser for each subnet and the primary domain controller maintains the domain-wide list.
Browsing takes place on every installed transport protocol. If you are running NWLink and TCP/IP, your browser searches for servers on the NWLink and TCP/IP. If you limit your protocols, you can increase your network performance. By limiting the number of protocols you limit broadcasts on the network. Your computer system responds faster when accessing the network, because it doesn’t have to timeout on several different protocols when trying to make a connection.
There are certain situations where a master browser is needed: a client can't find its master browser, client detects that a master browser has disappeared, or a windows NT Server starts on the network. Every time a master browser is needed on a segment, an election is held. You should configure a system on each subnet to be the preferred master browser in order to reduce network traffic caused by elections. You can even turn off servers from announcing themselves to the network. To turn off announcements type this command:
NET CONFIG SERVER /HIDDEN:YES
The browser election tries to find the most robust computer to be the master browser. A computer initiates an election by sending an election datagram out to the network. When a browser receives an election datagram, it examines the election criteria set on that datagram. If the browser has better election criteria, it sends out its own election datagram. This continues until no more election datagrams are broadcast. When a browser can't send an election datagram because it doesn't have better criteria, it attempts to find the new browse master. See Chapter 11 for more on browsing.
NT has networking built in. It ships with two redirectors that allow the computer to access the network. NT provides support for five protocols: NetBEUI, NWLink, TCP/IP, DLC, and AFP. TCP/IP is the default protocol when you install NT's networking components. TCP/IP and NWLink are routable protocols. NetBEUI is a small, fast, and efficient protocol for small networks; however, it is not routable.
NT uses IPCs to communicate between computers. RPCs are the most robust and mature of the IPC mechanisms. Other IPCs supported by NT are: NetBIOS, Winsock, named pipes, mailslots, and NetDDE.
You use the Server applet in Control Panel to manage your shared folders. In order to share folders, you can use Explorer or Server Manager. Once a folder is shared you should use the Server applet, which is also found in Server Manager.
Finally, you can improve the performance of your workstation and network by assigning a preferred master browser. Whenever a browser election occurs, network traffic is generated. By having a preferred master browser, you can help reduce the amount of traffic.
| NT bridges the gap between the OS and the NOS by providing built-in networking. | |
| The NT networking model is made up of layers, which loosely correspond to the seven layers of the OSI networking model. | |
| Be sure to understand that the TDI layer and the NDIS layer allow transport protocols to communicate with applications and networks seamlessly. | |
| NT uses redirectors to give client computers access to server services. | |
| Protocols are languages used by computers. |
| Data Link Control (DLC) is a gateway protocol. | |
| Know which protocols are routable (NWLink and TCP/IP) and which ones aren't (NetBEUI and DLC). Also know when you should use each protocol in a given situation. | |
| IPCs support two-way communications between computers. NT supplies six methods of IPC: NetBIOS, Windows Sockets, named pipes, mailslots, NetDDE, and remote procedure calls (RPC). | |
| Once a share is created, the best way to manage the share is through the Server applet in Control Panel. | |
| NT creates hidden shares for administrative purposes. Two hidden administrative shares are the C$ and the Admin$. | |
| The Computer Browser service maintains a list of available servers on the network and provides that list to the clients, when requested. |
1. Which of the following are advantages to implementing the redirector as a file system driver? (Choose all that apply)
2. Which layer of the OSI model does the NDIS layer of the Microsoft Networking model operate?
3. Which layer is between the TDI and the NDIS layers?
4. What does the TDI layer provide?
5. What is the importance of the NDIS interface layer?
6. What does the multiple UNC provider (MUP) do?
7. Which protocol could you use if you had two separate physical subnets connected by a router? (Choose all that apply)
8. Which protocol would you choose if you had a LAN with only 5 workstations and 1 server connected on a single physical subnet?
9. Which protocol is used mainly as a gateway protocol?
10. You want to connect two remote sites with a router, but don't want to waste time configuring a protocol. Which protocol should you choose?
11. You want to create a share on your workstation, but don't want it to be visible when users browse the network. How can you do this?
12. Which type of IPC is used when your computer broadcasts that it is joining a workgroup?
13. Your workstation has NetBEUI, NWLink, and TCP/IP installed on it. You notice that every time you browse the network, your computer takes a long time to display the available computer's list. Your friend doesn't experience any noticeable delay when browsing the network. What should you do to fix the problem? (Choose all that apply)
14. You have several folders shared on the network from your workstation. How can you check to see which folders have connections to them?
15. Which service allows your computer to be seen on the network?
16. You are developing a NetBIOS-compliant naming standard for your organization. You plan to use the following format: CityName-Bldg#-Rm#-FirstName. The cities where your network is installed are Dallas, Los Angeles, New York, and Orlando. Building numbers are all four digits and room numbers are all three digits. No one's first name is over ten characters in length. Will this work?