Chapter 1 * |
Introduction to Windows NT 4.0 Server * |
| Certification Objectives * |
| Windows NT Server Overview * |
| Preemptive Multitasking * |
| Multiple Process Management Models * |
| Programs * |
| Tasks * |
| Processes * |
| Threads * |
| True Multiprocessor Support * |
| Centralized Profiles and Policies * |
| Profiles * |
| Policies * |
| Built-in Remote Access Service (RAS) * |
| Fault Tolerance * |
| Backup Domain Controllers * |
| Multiple Network Interface Cards * |
| Directory Replication * |
| Hot Fixes * |
| RAID 1 and 5 Support * |
| Internet Information Server (IIS) and More * |
| Index Server * |
| FTP Server * |
| Gopher Server * |
| Administrative Wizards * |
| Windows NT Architecture * |
| User Mode versus Kernel Mode * |
| User Mode * |
| Kernel Mode * |
| Hardware Abstraction Layer (HAL) * |
| Windows NT Microkernel * |
| Executive Services * |
| Windows NT Subsystems * |
| Win32 * |
| MS-DOS * |
| Win16 * |
| OS/2 Subsystem * |
| POSIX Subsystem * |
| Windows NT Memory Organization * |
| Virtual Memory * |
| Demand Paging * |
| Linear 32-bit Address * |
| Device Drivers * |
| Certification Summary * |
| Two-Minute Drill * |
| Self Test * |
| Self Test Answers * |
| Answers to Chapter 1 Self Test * |
| Windows NT Server Overview | |
| Windows NT Architecture | |
| User vs. Kernel mode | |
| Executive Services | |
| Windows NT Subsystems | |
| Memory Organization |
Windows NT Server 4.0 is Microsoft’s latest release of their robust network operating system. In just a few short years of existence, Windows NT has proved to be a premier enterprise networking solution. The modular NT architecture provides for greater stability, performance, and fault tolerance. There are many modular components in the operating system, but the most important components are called the Executive Services, which perform their specific responsibilities while together maintaining the system as a whole. These Executive Services run in privileged mode, also known as Kernel mode, and have direct access to the hardware in the system. The other components are run in User mode and do not have this privilege. The majority of operating system code in Windows NT is run in User mode.
The ability to support high performance hardware, as well as differing processor architectures such as RISC-based processors, makes NT a candidate for even the largest enterprises. The improved memory architecture means you can run more applications at once. This is done by the use of virtual memory, which uses the hard disk to process data when RAM is not available.. The new 32-bit memory architecture supports large amounts of RAM, which is critical to server performance and enables you to run many applications at once. Applications also receive a performance boost, as well as increased stability and protection from misbehaving applications, which can bring down other applications or cause the system to hang. Support for existing applications is provided through the NT Environment Subsystems, which means you do not have to abandon your existing applications to migrate to Windows NT. Application support is critical to NT, and is very important to understand.
Windows NT began in 1988 as a project to make a more stable, secure, reliable operating system. After five years in the works, it was finally released as Windows NT 3.1 and Windows NT Advanced Server 3.1 in 1993. It was called 3.1 because of its similarity to the Windows 3.1 operating system that was so popular at the time. Although NT was a significant advancement over Windows 3.1, it did not gain much initial acceptance. However, this changed with the release of , Windows NT 3.5, which still had the familiar Windows 3.x user interface but included many enhancements and fixes. One significant change in NT 3.5 was the introduction of new names to differentiate two products: Windows NT Workstation for the workstation operating system and Windows NT Server for the network operating system.
Windows NT 3.51, the next version released, contained significant improvements such as long filename support, Domain Name System (DNS), Windows Internet Name Service (WINS), compression, and performance enhancements. NT 3.51 was the most successful version to date, but the best was yet to come for Windows NT Server.
With the release of Windows 95 and its very popular Start menu, Taskbar, Explorer, and shortcuts, it was no surprise that the Windows 95 user interface would become the interface for the next release of NT Server, entitled NT Server 4.0. Now easier to use, Windows NT 4.0 found a place in the market that challenged its most dominant competitor, Novell NetWare. With an integrated BackOffice suite of products for messaging, system management, database management, and internet connectivity, NT 4.0 Server quickly started outselling the competition. With the gaining popularity of NT, there also came a demand for skilled, professional administrators and engineers to support the product. By earning the designation of Microsoft Certified Systems Engineer, you will qualify to meet that demand.
Windows NT 4.0 uses preemptive multitasking to run several applications at once. Although these applications are not being executed at the same time, it appears that they are because the processor is executing threads that belong to each program. These threads have different priority levels that determine their order of execution. Threads with lower priorities must yield control to the higher priority task. Threads are also given a time slice of the processor that can expire. In preemptive multitasking, then, the operating system maintains processing control by assigning a priority and a time slice to each thread.
In previous operating systems the application did not yield control of the processor; this could cause all other active applications to stop responding, or it could even cause the entire system to hang. NT avoids this by preemptive multitasking and by running applications in a special way, as discussed later in the chapter.
The other method for multitasking is cooperative, or non-preemptive. This is how applications were run on older 16-bit operating systems such as Windows 3.x. The problem with cooperative multitasking is that the applications share an address space, and periodically have to check the message queue for other applications waiting for processing time. When an application fails to yield control of the processor, it can hang the rest of the programs or even the entire system. In order to maintain compatibility with older programs, Windows NT by default, cooperatively multitasks these 16-bit applications in a single Virtual DOS Machine (VDM), as discussed later in the chapter. Although the 16-bit applications are cooperatively multitasked by default within the VDM, they are preemptively multitasked with the rest of the applications running on the system outside the VDM.
With NT 4.0 you have the option of overriding this default and running each application in its own memory space. This can prevent interference among currently running 16-bit applications.
Let's look at a few concepts that help explain how NT can run so many applications at once—or multitask applications—so efficiently. A good way to understand the components of the operating system is to take a look at the information shown in the Windows NT Task Manager. This tool indicates what programs, processes, and threads are currently running on the system. Each of these elements is described in the following paragraphs.
A program is basically the application you are using, such as Microsoft Word or Excel. In Task Manager you can open the Applications tab to view a list of applications (programs) that are currently running. If an application is not responding, you can highlight it and end it.
Tasks are more difficult to explain because the term is used to describe many things. However, a task is most often used to refer to a program that is running. The name Task Manager is thus appropriate because it enables you to manage tasks that are running on your computer.
As you interact with a program, it creates one or more processes in order to carry out your instructions. In other words, programs spawn processes. Although it appears that a process is the application itself, this is not always true. A program can have more than one process, and each process contains at least one thread. Each process has its own address space so it does not interfere with other processes running on the system. This is not to be mistaken with applications that are run in separate memory with their own address space. The process address space for threads is protected whether or not the application itself is run in separate memory. In other words, you do not have the option of running a process in the same address space or not. This is within the operating system, and cannot be modified. The Process Manager of the Windows NT Executive is responsible for the monitoring of these processes.
A thread is the smallest unit of code. An application can create many threads, and each thread inherits the priority of the process that spawned it. A thread's priority can be adjusted up or down by two levels. For example, let's say a process spawned a thread that inherited the priority of 26. The priority of this thread can be increased to a priority level of 28. (Thread priority in NT ranges from a low of 0 to a high of 31.)
However, a thread cannot have its priority adjusted below its base (initial) priority value. That is, a thread's priority can be adjusted down two levels only if it had previously been increased. When the priority of the thread is increased by two levels by virtue of its being in the foreground, it can then drop two priority levels as it moves from the foreground to the background.
Threads are small so they can be processed quickly. This makes the system appear as if the applications are running simultaneously. If the threads were not small you would be able to see each program execute for a few seconds, then see the system switch to the next application. For even better performance the threads can be executed on any processor of a multiprocessor system, as discussed next.
The ability to add more processors to a server as needed is a very welcome feature of the NT Server operating system. This scalability allows you to adapt the operating system to the environment in which it will be performing. As shipped from Microsoft, Windows NT Server can support four processors, and OEM versions can support up to 32 processors. If your server requires more processing power you simply add another processor, rather than reinstalling the operating system and applications on another, more powerful server.
There are two categories of multiprocessing:
| Asymmetric Multiprocessing (ASMP) | |
| Symmetric Multiprocessing (SMP) |
Windows NT is an SMP operating system, which is the multiprocessing method of choice. The following paragraphs describe both types of multiprocessing, along with the advantages and disadvantages of each.
ASMP uses one processor for the operating system functions, and any other processors are assigned to handle user threads. Since the operating system resides on a separate processor, it is fairly easy to add more processors, as needed, for application processing. The disadvantage of ASMP (in an example where the system uses two processors) is that one processor can be nearly idle while the other processor is being heavily used. The processor that is idle cannot assist the other processor because it is reserved for one of two functions: either the operating system or the applications.
This problem is resolved with SMP, where threads can be run simultaneously by any processor in the system. In addition, the operating system itself, which can tax system resources because of all the processes it generates, is able to use all available processors. This provides a significant performance increase. If the operating system is performing many executions, it can take advantage of idle processors in SMP. With ASMP, the operating system can only use the processor to which it is assigned.
When resources such as profiles and policies are centralized, it is much easier for the system administrator to manage them. The domain structure in NT lends itself to centralized administration of these resources through tools such as User Manager for Domains and System Policy Editor.
User Manager enables you to create a mandatory user profile for all of your users, or a different profile for each group of users. This can be useful for differentiating the needs of different departments, such as Payroll, Accounting, and Sales. You can tell Windows NT which groups the user belongs to, and NT will apply the corresponding user profile.
You can also employ user profiles to create profiles for different types of systems, because a profile will not work correctly if the system does not support it. For example, let's say you have a user profile that has a Super VGA screen resolution and one of your computers that uses the same profile only supports VGA. In that case the screen will not look correct. The centralized placement of these user profile makes it easier for you to update the profile as needed, rather than updating each user's profile individually. You can make changes to user profiles on a single-user basis, but if you have many users this can become a time-consuming task.
A mandatory user profile prevents users from changing settings, which may be desirable for your organization. If you do not want to restrict users in this way, you can still assign user profiles, but not make them mandatory. This will let users save their changes to the desktop, yet allow other users on the system to receive their own settings when they log on.
Users can also have what is known as a "roaming"—or personal —user profile, which will maintain their personal settings for every computer they log on to. For example, a user with a roaming profile can log on to a computer that they have never logged on to, and their desktop settings will be identical to the settings on their own computer. Any changes made to the roaming user profile will be incorporated for use the next time they log on.
The use of the System Policy Editor can restrict what users can do, as well as what they can access on the system. With a system policy in place, the operating system looks in the Netlogon folder on the logon server for a file called NTConfig.pol. If this file is present, the contents are copied to the users' registry. The contents of the NTConfig.pol file overwrite the corresponding parts of the default file. You can have special settings for specific users or you can create groups that receive different settings that you specify. By using a combination of the NT profiles and policies tools, you can greatly customize environments and can restrict access for users and groups on your network.
Remote Access Service (RAS) enables users to connect over a phone line to your network and access resources as if they were at a computer connected directly to the network. Once a user is connected and authenticated, the phone line becomes transparent to the user. This is very important for traveling users who must remain in contact with the network for e-mail and transfer of data. They have access to the same file, print, and database servers that they would have at the office. This enables users to work at home, and still submit their files, print reports, and execute database queries. Here are a few features of the RAS:
| Callback ability | |
| Restrict access from the network to RAS Server only | |
| Use of integrated NT security | |
| Encryption |
When Windows 95 was introduced, it used the term Dial-Up Networking to refer to remote access, and Windows NT 4.0. Server now uses that term. All previous versions of Windows NT referred to it as the RAS client. The two terms are interchangeable.
When working on the client workstation, you will be working with Dial-Up Networking to configure the connection. However, on your NT Server you will be using the Remote Access Administrator to manage the dial-in process. This utility enables you to start and stop the RAS services, send messages, disconnect users, and grant or revoke remote access for users or groups.
You can also grant or revoke access for dial-in by using the User Manager for Domains. This tool enables you to specify three different settings for callback security:
You can have the RAS server call the user back at a predefined number.
You can have the user specify the number where they would like to have the server call them back. This is not as secure, but it may be necessary for mobile users who are always at different locations such as hotels and airports.
The last option is to not call the user back.
There are many types of clients supported through Windows NT RAS: Windows NT, Windows 95, Windows 3.x, MS-DOS, and any other Point-to-Point protocol (PPP) client. TCP/IP, IPX, and NetBEUI protocols are also supported. If you are using TCP/IP to connect to your RAS server, you can automatically be assigned an IP address. You will learn more about dynamic assigning of IP addresses—and TCP/IP in general—in later chapters of the book. This wide range of support makes it easy to implement RAS in your organization and it is largely responsible for the popularity of RAS. Your laptops can have Windows 95 installed and still be supported, and your home users can have Windows 3.x and still be supported.
With the important role that computers play in today’s businesses, downtime or data loss is unacceptable. A business can lose thousands of dollars for every hour that a computer system is not functioning. With this in mind, companies go to great lengths to protect their systems. In mission-critical networks, computers must be fault tolerant. Fault tolerance is the ability of a computer to ensure that data and resources remain functional in the event of emergency. This can be achieved with a combination of hardware and/or software techniques, and the solution will vary in price and protection. For example, a fault-tolerant hard drive array will allow a failed hard drive to be removed from the system and replaced while the system is still running. The data from the failed hard drive can even be regenerated without any user intervention. Windows NT provides many built-in fault-tolerant features such as:
Backup domain controllers
Multiple network interface cards
Directory replication
Recoverable file system
Hard disk mirroring, duplexing, and striping with parity
These features are described in the following sections.
It was 1:30 in the morning when I wrote this, so e-mail me if you would like it different, longer, shorter, or better. J When you are participating in a domain, which is a logical grouping of computers, the presence of Backup Domain Controllers (BDCs) will ensure fault tolerance by having multiple servers available to authenticate users. These domain controllers provide central support for user and resource management. The Primary Domain Controller (PDC) is in charge, and will replicate changes to the BDCs. In the event that a PDC is not available, the BDCs can also be promoted to PDC. If the PDC does not come back online, the BDC can continue as the PDC. If the PDC does come back online, you can demote the second PDC down to BDC again, and continue as you did before. You have the option during installation of NT Server to choose between a PDC, a BDC or stand-alone server. Make the correct decision, because once you have installed NT as a domain controller, you will have to reinstall the operating system to change it. There is also no way to promote a stand-alone server, sometimes referred to as a member server, into a domain controller without reinstalling NT.
Multiple network cards in a computer can provide fault tolerance by placing a computer on two segments of a network, or they can be used to connect two networks. Windows NT Server acts as a router that routes packets between the two segments or networks.. This is a common solution for organizations that cannot afford a high quality router, but would still like to route packets to another network. Should one of the other links fail, NT can also be used as an alternate route between two segments or networks. This is most often used with larger network implementations.
The purpose of directory replication is to make an exact copy of a folder and place it on another server. Replicated information could include logon scripts, databases, or any information that is accessed by many users. By replicating this information, you can load balance servers so that one server is not overburdened with excessive traffic. For example, let's say you want to replicate a logon script that you have created and place it on all of the other domain controllers. This is accomplished by placing the information you would like to replicate in the proper export directory, and choosing which servers can import this data. The Directory Replicator service will run on both the import and export servers to ensure the replication process goes smoothly.
You can adjust the rate at which replication occurs. If you are replicating a script that is rarely updated, then it would make more sense to increase the amount of time between replications.. If you are replicating a database that must remain consistent, you would decrease the amount of time between replications, to ensure that the latest changes are being copied to the import servers. Replication updates occur automatically. After you set up the replication, the Directory Replicator service maintains the replication process. To replicate a directory, just put the name of the directory you want to replicate in the export box.
Here is the path to the export directory for Windows NT Server 4:
Any directory that is found or created under this directory is available for export. You must place the files in a directory under the export directory for them to be replicated. You cannot just place files in the export directory.
The import directory for the receiving computer is:
This directory path is created automatically when replication occurs. Check this directory to verify that the replication process went as planned.
When an error occurs because of a bad sector, the file system moves the data that was located in this sector (if possible) to another sector, and labels the original sector as bad. This hot fix is transparent to the user and to the applications. You will not even be aware that it is taking place. However, there is a possibility that you will lose data. This would never happen on subsequent attempts to access information on this sector because it has been marked as unusable. Hot fixing is a feature of NTFS and SCSI hardware, and is not supported for the FAT file system.
Redundant Array of Inexpensive Disks (RAID) can be used for fault tolerance within the disk subsystem. RAID technology uses multiple hard drives to provide performance and/or fault tolerance through mirroring or striping data. Windows NT RAID support is done through software support. A hardware RAID implementation produces better results, but it costs more. Notice that there are many levels of RAID support, each with varying degrees of performance and fault tolerance. Windows NT supports three levels of RAID: levels 0, 1, and 5. However, only RAID levels 1 and 5 are fault-tolerant.
| RAID 1 uses disk mirroring to duplicate information to another hard disk. in this method, the operating system writes information to both disks for each operation that is performed. If one of the hard drives fails, the other hard drive is immediately available with the very same information. This provides 100 percent fault tolerance, but only allows you to use fifty percent of your total hard disk space. The other fifty percent is being used for the mirror. That is why this implementation is considered more expensive. You do get a slight increase in performance, because the first available disk is used to service a request. |
A technique similar to disk mirroring is disk duplexing. This method maintains a mirrored drive, but includes another disk controller, rather than using the same controller for both hard drives. This increases performance and provides fault tolerance against both controller and hard drive failures.
| RAID 5 uses a method of striping data across several hard drives, with parity information also included. This parity information is striped across the drives, rather than being stored on a single hard drive. (Storing information on a single hard drive is the equivalent of RAID level 4.) With the addition of parity, you can recreate the information that was stored on a drive if it were to fail. Just like mirroring, this method is 100 percent fault tolerant. However, you do not waste as much valuable hard disk space as you do with mirroring. Also note that it takes a minimum of three hard disks to implement disk striping with parity. You receive a performance boost with a RAID 5 implementation due to the fact that multiple drives are reading information at the same time. However, it takes more time to calculate the parity information. |
Microsoft has included its Internet Information Server (IIS) with NT Server to make it easy for you to connect your organization to the Internet, or to create an Intranet to browse your organization's internal resources. You have the option of installing IIS 2.0 when you are installing NT Server or any time thereafter. What is unique about the Internet Information Server is that it is free. This may be an effort to convince business that IIS could be used to as a low cost (or no cost) alternative to the other Web servers on the market today. Microsoft hopes that you will see the value in their Web server and begin using it. However, IIS will not run on anything other than Windows NT, so you must have an NT Server in order to take advantage of IIS.. In addition to providing the basic features of IIS, Microsoft offers additional BackOffice products to enhance its functionality. Microsoft Proxy Server is for connecting your network to the Internet. Microsoft SQL Server for connecting databases to IIS for viewing and updating information in the database over the network or Internet. You can also read your e-mail through a Web browser with Exchange Server. These are just a few of the possibilities that exist with IIS.. Since the popularity of both NT Server and the BackOffice suite have greatly increased, we urge you to become certified in these products. By becoming certified, you demonstrate your ability to support the IIS and the various products that take advantage of it.The following sections describe the features that are part of the IIS and explain theservices they provide for NT Server.
The Index Server, provided with IIS, enables you to index all HTML documents and other supported formats. It has the ability to find text in HTML documents, as well as Word, Excel and various other text documents. When you have indexed all of your data, you can query that data using keywords to bring up documents that contain the desired information.. This is just like using an Internet search engine to find what you are looking for.(Quite possibly the search engines are also using Index Server to index information.) Once you tell Index Server what information to index, it performs the tasks; it also continues to index new documents as they are added to the server.
You can use the File Transfer Protocol (FTP) server to upload or download information within your company, or outside your company via the Internet. Having an FTP site is useful when outside sources need to send or receive information that is too large to be attached to e-mail. Many organizations provide FTP services along with Web services for making software updates, patches, and drivers available to the public. Although FTP is slowly becoming replaced by the Web, it is by no means dead. FTP still has widespread acceptance in the Internet community, even though it is not as user-friendly as the Web.
A Gopher server is included with IIS, although the popularity of the World Wide Web has made Gopher nearly extinct. Gopher can be used as an index to look for information on the Internet, or on your own company's Intranet. You can use menus to access text files that are available on the Internet. Gopher is easy to use, has the ability to create links to other computers, and enables you to make your own menus.
NT 4.0 Server includes a number of Administrative Wizards that help you perform common administrative tasks. They do not contain any added functionality—they simply guide those unfamiliar with NT 4.0 Server through the basic operations. After you are comfortable with the Administrative Wizards, you should be ready to venture out on your own. Eight Administrative Wizards are currently available:
| Adding user accounts | |
| Group management | |
| Managing file and folder access | |
| Adding a printer, either local or network | |
| Add/Remove programs | |
| Install a new modem | |
| Network client administrator(installs or updates client workstations) | |
| License compliance (checks licensing for installed applications) |
Windows NT architecture is unlike any other operating system in Microsoft’s arsenal. Many of Microsoft’s operating systems—such as MS-DOS or Windows 3.x— require DOS; some argue that Windows 95 stills needs DOS. However, NT has no DOS code at all. This is amazing when you consider that NT can still run DOS and older Windows 16-bit applications. Not only can it run these programs, but in some cases they will run better than in their native environment! If you have been using NT Server since the first version, you may not have seen drastic changes to the architecture with each new version, but NT 4.0 is significantly different from other operating systems. The next sections will describe the architecture that makes NT unique.
An important feature of Windows NT, and one that contributes to the great stability of its architecture, is the use of two types of operating mode. The two modes, User mode and Kernel mode, differ primarily in the amount of privilege assigned to each. User mode cannot directly access the hardware, whereas Kernel mode can. Figure 1-1 is an overview of the NT architecture, showing the role of User mode and Kernel mode.
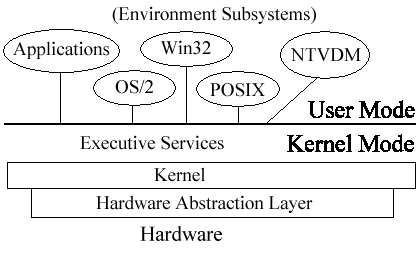
Figure 1-1:User mode versus Kernel mode
User mode, often referred to as non-privileged processor mode, is where most of Windows NT code is located. This is also where applications and the various subsystems are run. This mode cannot communicate directly with the hardware, and must call upon the operating system to make these calls. This provides stability for the operating system by creating a protective barrier from misbehaving applications, which could possibly bring down the entire operating system.
Kernel mode—commonly referred to as privileged mode—does have direct access to hardware and software resources in the system. Applications that require hardware functions must be translated into these Kernel mode instructions. The Kernel mode must translate the calls from User mode before the hardware can be accessed, and then must pass the data back to User mode. An important note about the release of NT 4.0 is the fact that some components of NT that used to run as User mode components now run as Kernel mode components. These include the Window Manager, the graphical device interface (GDI), and graphics device drivers. With these components running in Kernel mode, there should be an increase in graphics performance because you no longer need to translate the calls back and forth between the two modes.
The User-mode applications never call the hardware directly, because these calls are handled by the Windows NT Executive. Similarly, the Hardware Abstraction Layer (HAL) separates the kernel from the hardware to provide an intermediary layer so that the Windows NT kernel does not have to communicate with the hardware. The HAL is the most common reason why some DOS and early Windows applications are incompatible with NT. These applications expect to communicate directly with the hardware, and will not run if they are not given this privilege. Although this appears to be a disadvantage,, it is actually an advantage because the HAL provides increased protection from errant applications. However, the HAL increases system complexity. Not only do you need a separate HAL for each hardware platform, but you need two HALs for each processor architecture—one to support a single processor, and another to support multiple processors.
The term microkernel, or kernel, refers to the core of code in an operating system. This is the most important part of the operating system and is responsible for all functions on the system. However, the kernel cannot do this all by itself. It requires some other components to be responsible for their own functions, leaving the most important tasks to the kernel. As an analogy, think of the CEO of a company. The CEO does not have be a part of every decision that is made at the company, but instead relies on other people such as the President, Vice-President, and various managers of the company. However, when a decision has to be made that will affect the entire company, it is escalated to the CEO, who takes all of the information gathered by the Executives and uses that information to make an appropriate decision. In Windows NT, the operating system kernel calls upon the services of the Windows NT Executive, just as the CEO called upon the corporate executives to provide critical information. NT's modular architecture allows portions of the operating system to be rewritten or replaced as needed. It also facilitates the integration of new components into the architecture.
The NT Executive Services (also called System Services) provide the operating system services that the kernel is too busy to perform. The kernel is actually part of the NT Executive, and together they are responsible for the entire system. The NT Executive includes the following operating system components:
| Object Manager is responsible for managing objects, which are used to represent resources in the system. | |
| Security Reference Monitor (SRM) is responsible for enforcing the security policies by verifying credentials for users and groups. | |
| Local Procedure Call Facility (LPC) is responsible for processes that share information between each other on the local machine. | |
| Process Manager monitors the status and usage of processes and threads. | |
| Virtual Memory Manager (VMM) manages the system's virtual memory pool, in which the hard disk is used to simulate RAM. | |
| I/O Manager is responsible for all input and output for the file system, I/O devices, and redirectors. | |
| Win32 Window Manager and GDI. These components had been in the Win32 subsystem in previous versions of NT, but were moved to the NT Executive in version 4.0 |
Figure 1-2 summarizes the Executive Services of Windows NT 4.0.
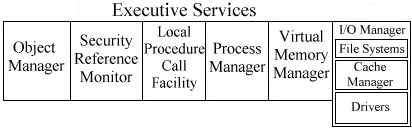
Figure 1-2:Windows NT Executive Services
Windows NT maintains compatibility with existing applications through the use of an environment subsystem that mimics the environment that the application expects to see. Figure 1-3 illustrates some examples of environment subsystems. If a subsystem for a specific environment were not included in the operating system, there would be no backwards compatibility with non-NT applications using that environment. Subsystems for some of the infrequently used environments, such as POSIX and OS/2, can be loaded as needed. This saves memory because they need not be loaded at system startup. However, the Win32 primary subsystem is always created at startup.
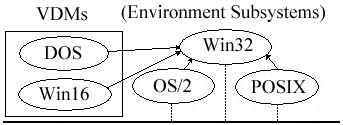
Figure 1-3:Windows NT environment subsystems
Notice that these services are referred to as "subsystems" because they can perform independently of any other subsystem. These subsystems run completely in User mode and each is isolated from other subsystems; this is why they are sometimes referred to as "protected" subsystems.
As shown in Figure 1-3, Win32 is the primary subsystem for NT, and it is responsible for all user input and output. The Win32 subsystem is also responsible for receiving requests from the other environment subsystems. Win32 used to have the GDI and USER components in the Win32 subsystem, but they have been moved to the NT Executive in the release of NT 4.0. Two subsystems, MS-DOS and Win16, actually belong to the Win32 subsystem. The Win32 subsystem provides a 32-bit, preemptively multitasked environment, where each application receives its own address space for greater stability.
The MS-DOS subsystem is quite possibly the most important subsystem in NT for compatibility. The DOS environment is called the virtual DOS machine (VDM). The VDM fools the DOS application into thinking it is the only application running, just as it was run in the DOS operating system. The VDM is a 32-bit application run in a separate memory space that is capable of being multitasked with other applications (thereby increasing performance). This subsystem will run DOS applications, but it will also run Windows applications that require DOS.
Since 16-bit Windows applications run over DOS, they must be emulated in this way to work with Windows NT. This is achieved by running the VDM and an emulator called the WOW— short for Win16 on Win32. When a 16-bit application is run, it will have to have the Win16 calls translated into Win32 calls, or vice versa. This is done by a process known as thunking. It is much easier to make the Win16 call to Win32 because you just have to add bits, whereas it is much more difficult to go from Win32 to Win16 because you cannot just drop bits.
For 16-bit applications that expect to share address space with other 16-bit applications, the applications are run in a single VDM. Although the 16-bit Windows applications are run in the same memory space by default, they do have the option of being run in a separate memory space. If the applications are run in a shared memory space, there is an increased possibility that one faulty 16-bit application will bring down every application that is sharing the memory space. When the applications are run in their own separate memory space, any application that crashes only affects itself— not other applications currently running outside of the memory space. This is a welcome feature for users of many older 16-bit applications that had trouble with misbehaving applications in the past.
The OS/2 subsystem is the most limited of the subsystems provided with NT. There is less need to create a fully functional OS/2 subsystem because support for the OS/2 environment has dwindled. Although the OS/2 subsystem is a 32-bit, multitasking protected subsystem, it can only run character-mode applications; it cannot run graphical applications. Interestingly enough, the OS/2 interface was going to be the primary subsystem for NT until the surprising popularity of the Windows 3.1 operating system. This made the Win32 primary subsystem a more logical choice.
The POSIX subsystem is included to support open standards, mostly for application support for UNIX platforms. In order to be POSIX-compliant, the software must fulfill certain requirements, such as case-sensitive filenames, hard links (which can be compared to Windows NT shortcuts, in which many entries can point to the same file), and additional time stamping. The POSIX subsystem is a 32-bit, multitasked, protected subsystem; however, you will not have many opportunities to take advantage of it because of the lack of support.
The memory organization of Windows NT is built around three main concepts: virtual memory, demand paging, and a 32-bit flat address space. Each of these methods helps Windows NT provide memory for applications, even when the amount of physical memory has been exceeded.
Windows NT uses virtual memory to simulate RAM on a computer when more memory is needed. It does this by using the computer's hard disk as needed. Figure 1-4 illustrates how data can be moved from RAM to hard disk. When the computer is not using a portion of data in RAM, the data can be swapped in 4K pages to the hard disk and replaced with data that is currently needed.
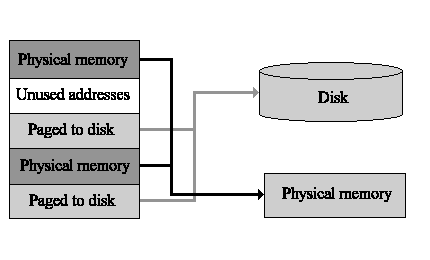
Figure 4: NT memory organization
Of course, RAM operates much faster than the hard drive, so virtual memory is no substitute for having enough RAM in your system. In older operating systems such as DOS, when you did not have the luxury of virtual memory, the application would not run at all. To accomplish this process, a component of the Windows NT Executive called the Virtual Memory Manager (VMM) is used. The VMM is responsible for mapping the virtual addresses to the physical pages of computer memory. The VMM is also responsible for the actual paging process, which will be described later in this book.
Demand paging is the process of swapping the information from disk or memory in 4k pages as needed. This process requires the use of the NT paging file, which is an actual file on your hard disk reserved for this use. If your paging file is not large enough, you will see error messages that your system is running low on virtual memory. You will learn more about configuring the paging file in later chapters of the book. For now, you just need to understand that the hard disk will be used when your physical memory is exceeded. You can tell that the hard drive is being used for paging when you hear the hard drive make noise as you switch to another open application If you had enough RAM, the switch would be instantaneous. Try opening several applications and switching among them to see when your system begins using the page file. You can also bring up the Windows NT Task Manager and view the available physical memory from the Performance tab.
Another term to keep in mind is thrashing. Thrashing sounds much worse than paging, and it is. When you have exceeded the amount of physical RAM in the system, and your paging file is becoming full, the system will begin thrashing to look for more available memory. This is a not good for the system, and you should take corrective action, such as adding more physical memory or increasing the size of your paging file.
Applications use a 32-bit linear address when they access memory. This is different from the segmented scheme used for MS-DOS and other versions of Windows. With the segmented memory scheme, an application accesses memory by using a segment and an offset; the combination of these two coordinates can identify a memory address. It is comparable to a grid which has rows and columns. To find a location on the grid you find the appropriate row (the segment), then find where it intersects with the column (the offset). The computer required extra time to compute location using this segmented memory scheme; ittook even more time for software developers to use this method, because it was difficult and slow.
With the linear 32-bit address, the first address starts at zero, and continues in one-byte increments until the system is out of physical memory. Since memory allocated in this way must use unique addresses, a 32-bit address gives you 4 GB of address space. Two gigabytes of this address space is reserved for the applications to use, and the other 2 GB is reserved for the system's use. This linear addressing makes NT more compatible with different processor architectures because more RISC processors (and even some CISC processors from Intel) use linear addressing.
Device drivers enable your system to communicate with the various devices in your system. A driver is basically a small application that the operating system calls when it needs the device to perform a function. A well written driver is important for the stability and performance of your system. A wrong or poorly written device driver will not maximize your performance, and it may cause system problems or just not work at all with the device. Since the driver must communicate with the device to perform a function, you can see how important it is to make sure you have the correct version of the driver. Older drivers for Windows 3.x or Windows 95 will not work with NT, and previous NT versions of drivers may not work either. Microsoft has provided many compatible drivers for use with the operating system, but may not have current drivers for brand new devices. The device vendors may also provide new drivers for NT 4.0 on their Internet Web sites. The good news is that drivers are continually updated. The bad news is that there are still not that many available for NT.
Windows NT Server was created as a high performance network operating system that is optimized for resource sharing. This chapter described the features that increase performance such as preemptive multitasking of applications and the how processes spawn threads of differing priority. Priority of these threads is inherited from the parent process, but can be adjusted. Not only can you multitask applications, you can add more processors to the NT system to take advantage of multiprocessing. This allows threads to run on any processor in the system. Fault tolerance is supported by the use of hot fixing, the use of Backup Domain Controllers, multiple network cards, directory replication, and RAID support. The Redundant Array of Inexpensive Disks offers varying levels of performance and fault tolerance, of which NT supports levels 0, 1, and 5. Levels 1 and 5 are mirroring and disk striping with parity respectively. These are both capable of withstanding hard disk failure.
Integrated with Windows NT Server is the Internet Information Server (IIS). This Web server allows you to run your own Web page on the Internet or your company's Intranet. IIS comes with Index Server, and both FTP and Gopher servers.
Under Windows NT architecture, the chapter covered the two modes that portions of code and applications are run in: User mode and Kernel mode. Kernel mode has direct access to the system resources whereas User mode does not. The Hardware Abstraction Layer (HAL) is used as an intermediary between the hardware so the NT kernel does not have to communicate directly with the hardware. The kernel is the core of the operating system, and the head of the NT Executive Services. The kernel and the Executive Services are responsible for the entire system. Windows NT maintains compatibility with existing applications through the use of an environment subsystem that mimics the environment the application expects to see. Examples of environment subsystems are the POSIX, OS/2, and Win32 subsystems. The DOS and Win16 subsystems are actually housed within the Win32 subsystem. Since the DOS and Win16 subsystems are a part of the Win32 subsystem, they also run in User mode. They are also preemptively multitasked with other applications on the system, and protected from each other. They both need to call upon the Win32 subsystem, which is the primary subsystem that handles these requests in NT.
The memory organization of Windows NT is built around three main concepts: virtual memory, demand paging, and a 32-bit flat address space. Virtual memory uses the hard drive to simulate RAM as needed. Demand paging is the process of swapping pages of memory between the hard disk and memory. The 32-bit flat addressing scheme is an improvement over the segmented memory method. The 32-bit scheme, which allocates addresses in one-byte increments until the physical memory is all gone, allows for 4 GB of virtual memory.
| Preemptive multitasking is the ability to run several applications at once. | |
| Task Manager for Windows NT is a tool that gives you dynamic data for the various programs, processes, and threads that are currently running on the system. | |
| As shipped from Microsoft, Windows NT Server can support four processors, and OEM versions can support up to 32 processors. | |
| There are two categories of multiprocessor support: Asymmetric Multiprocessing (ASMP), and Symmetric Multiprocessing (SMP). Windows NT is a SMP operating system. | |
| Use of the domain structure in NT lends itself to centralized administration of profiles and policies, through tools such as User Manager for Domains and System Policy Editor. | |
| Remote Access Service (RAS) enables users to connect over a phone line to your network and access resources as if they were at a computer connected directly to the network. Features of the Remote Access Service are: |
| Callback ability | |
| Restrict access from the network to RAS Server only | |
| Use of integrated NT security | |
| Encryption |
6. What would be the first step in the replication process if I placed my file to be replicated in this directory? C:\systemroot\SYSTEM32\repl\export
8. (True/False) RAID level 5 uses a dedicated drive that holds parity information for fault tolerance.
9. (True/False) Environment subsystems are run in the User mode.
10. HAL stands for _______________ _____________ ___________.