| TCP/IP Review | |
| Subnetting Versus Supernetting | |
| Decimal to Binary Address Representation | |
| Bit Swiping | |
| Determining IP Addresses Within Subnets | |
| How to Subnet a Class A Address | |
| How to Subnet a Class B Address | |
| How to Subnet a Class C Address | |
| Supernetting |
The current Internet Protocol, version IPv4, allocates 4,294,967,296 addresses for general Internet use. Sounds like a lot of addresses, but with the number of Internet users doubling in less than a year, these addreses are quickly used up. This has called for leading experts to devise what is known as IPv6 or IPng (next generation). Until the appropriate hardware is available to handle IPv6 we have to come up with a way to patch what is already in place and make it work a little longer.
Throughout this chapter we will discuss the various classes of IP addresses and the basis for subnetting within them. We will also cover in detail the available networks within each class.
With the Internet growing as large as it has, experts found that the two-level hierarchy of the addressing scheme was not meeting the demand for the number of networks.
As organizations grow in size, one network ID cannot meet the demand. The only answer is to implement a series of subnetworks. Subnetworks handle the limitation on the length a single medium can reach. If you have a large university campus that you must internetwork, you may not be able to cover the distance required with today’s communication mediums. Creating individual subnetworks would be the right approach to this internetworking challenge.
Some organizations are large enough to experience network congestion. With a large number of hosts communicating all at once on one network, the network can be become bogged down with transmissions. This is where subnetworks come into play; by having many smaller networks, congestion isn’t an issue.
The two-level hierarchy basically helps with routing the information to the appropriate host on a particular network. To do this you have to have a network address and a host address. An IP address is a 32- bit number made up of 4 octets. The IP address is split into the network address and host address between octets. Figure 4-1 shows a network with three subnetworks.
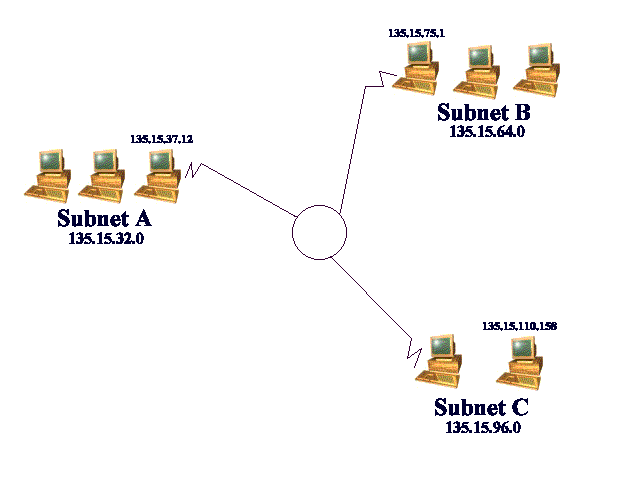
Figure 1: A Network with Three Subnetworks
Let’s take two IP addresses, 210.168.10.12 and 210.168.11.15. Looking at these two IP addresses without knowing anything else, you could not tell whether they are on the same network. But if you know that the first 3 octets specify the network ID and the last octet specifies the host, then you know that these two IP addresses are on different networks. If the first 2 octets specify the network ID, then these two addresses would be on the same network. You determine which bits or octets are used for the network address and which are for the host address by a term called masking. Allocation of network IDs and host IDs take careful planning. With the various needs and sizes of networks today, a system is needed to accommodate them.
One way that designers tried to accommodate the various size networks was classful addressing, which is based on the three distinct address classes: A, B, and C. The ranges for each class of IP address are determined by the first octet of the IP address (see Table 4-1).
| CLASS | First Octet Range |
| Class A | 1-126 |
| Class B | 128-191 |
| Class C | 192-223 |
Table 1: Octet Ranges Within Each Class
For example, if an IP address is 131.40.35.129, then this is considered a Class B address. From Table 4-1 you notice that 127 is not used. This particular octet was set aside for the loopback and diagnostic functions. Anything above 223 is not used in the first 3 classes. Classes D and E exist but are not relevant to Windows networking at this point in time.
As we mentioned earlier, there has to be something to tell us what kind of address it is and which octets are the network ID and which are the host ID. To do this we need a subnet mask. A subnet mask basically masks or denotes a portion of the IP as the network address and the other as the host address.
It is not always easy to determine whether two hosts are on the same network by comparing their network IDs.
Some cases are obvious:
151.173.28.160 Class B
217.63.143.230 Class C
Since these two addresses are in different classes, the hosts must be on different networks.
And some cases are not so obvious:
131.107.35.200 Class B
131.107.61.26 Class B
Since these two addresses are in the same class, the subnet mask must be used to determine if the hosts are on the same network.
If you use the default subnet mask of 255.255.0.0, then the hosts are on the same network. This can be proven with the ANDing process:
131.107.35.200 10000011 01101011 00100011 11001000
255.255.0.0 11111111 11111111 00000000 00000000
ANDing 10000011 01101011 00000000 00000000 (a)
131.107.61.26 10000011 01101011 00111101 00011010
255.255.0.0 11111111 11111111 00000000 00000000
ANDing 10000011 01101011 00000000 00000000 (b)
The ANDing results (a) and (b) in the same value; therefore the hosts are on the same network.
Now let’s use the subnet mask of 255.255.240.0:
131.107.35.200 10000011 01101011 00100011 11001000
255.255.240.0 11111111 11111111 11110000 00000000
ANDing 10000011 01101011 00100000 00000000 (a)
131.107.61.26 10000011 01101011 00111101 00011010
255.255.240.0 11111111 11111111 11110000 00000000
The ANDing results in a different value. Look at the third octets. Since the values are different, the hosts are on a different network.
Now try the subnet mask of 255.255.224.0 on your own.
This should result with the hosts being on the same network.
With classful addressing each class designates a certain series of bits for the network portion of the address and a certain series of bits for the host portion of the address. With Class A addresses the first eight bits, or first octet, determine the network ID and the last 24 bits, or 3 octets, determine the host ID. For example, if you have the following IP address:
10.123.45.16
10 is the network address. Any IP address beginning with 10 would be on the same network. Any IP address beginning with an octet other than 10 would be on a different network. The remaining portion on the IP address denotes the host. This particular host has an address on 123.45.16.
With Class B addressing the first 16 bits, or first two octets, determine the network ID and the last 16 bits, or last two octets, determine the host ID. For the following IP address:
150.213.92.12
150.213 is the network address and the last two octets, 92.12, are the host address. All IP addresses beginning with 150.213 are on the same network.
With Class C addressing the first 24 bits, or first three octets, determine the network ID and the last 8 bits, or last octet, determine the host ID. For the following Class C address:
210.211.10.1
we know that all machines with IP addresses beginning with 210.211.10 are on the same network. The last two octets, 10.1, signify the host address.
As we learned in Chapter 3, there are default subnet masks within each class of addresses (see Table 4-2).
Class |
Default Subnet Mask |
Class A |
255.0.0.0 |
Class B |
255.255.0.0 |
Class C |
255.255.255.0 |
Table 2: Default Subnet Masks
Remember that the subnet mask designates which portion of the address is the network address and which portion is the host address. This is done by converting the address to binary. 255 in binary is 11111111. The number 0 in binary is 000000000. The decimal number 255 in binary is eight 1’s and the decimal number 0 is eight 0’s. With the default subnet mask anything with all 1’s is considered part of the network address. Anything with all 0’s is part of the host address.
Let’s look at this again as a review. Take the IP address 10.123.45.16 and the subnet mask 255.0.0.0. We convert the subnet mask to binary and come up with:
1111111.00000000.00000000.00000000
If you draw a line where the 1’s stop and 0’s begin, you come up with:
11111111 | 00000000.00000000.00000000
If we draw a line at the same spot in the IP address, we have the following:
10 | 123.45.16
We can now see that 10 is the network address and the remaining octets are the host address.
In 1985 designers came up with RFC 950, which deals with the Internet Standard Subnetting Procedure. Within RFC 950 the designers discuss adding a third level to the hierarchy, the subnetwork address. Table 4-3 shows a comparisonbetween the original two-level hierarchy and the new three-level hierarchy.
NETWORK I.D. |
HOST I.D. |
|||
NETWORK I.D. |
SUBNET I.D. |
HOST I.D. |
||
Table 3: Two-Level Hierarchy Versus Three-Level Hieararchy
The three-level hierarchy adds a third component to the routing process, the subnet address, which takes a 4-octet IP address and divides it up three ways. This is known as bit swiping. It involves separating the IP address in the middle of an octet as shown in Figure 4-2.
| 1 | |2 3 |
| 2 3 4 5 6 7 8 9 0 1 2 3 4 5 | 6 7 8 9| 0 1 2 3 4 5 6 7 8 9 0 1 2|
| N E T W O R K A D D | SUBNET| H O S T A D D R E S S |
Figure 2: Bit Swiping to Create a Subnet Address
We will discuss bit swiping more later on. But a basic understanding of it now will help in the following couple of sections.
Supernetting came about when medium-sized organizations were having difficulty with the standard addressing scheme.
Class A addresses were entirely too large for them and most Class A addresses were taken by this point in time anyway. Medium-sized organizations needed a Class B or C address. The only problem is that there is a vast difference between these two classes in the number of hosts.
With Class C addresses you get 254 hosts out of every Class C network address. For many organizations this was not enough host addresses. So the first thought would be that any organization that cannot fit into the boundaries of a Class C address would need either a series of Class C addresses or a Class B address. With the limited number of class C address available, a medium-sized organization using multiple class C addresses was not feasible. Moving to a Class B address makes some sense, but then you have 65534 host address available. Again, this is not really a good answer, as many host addresses would potentially go to waste. This is where supernetting comes into the picture.
In 1992 RFC 1338 ( An Address Assignment and Aggregation Strategy) proposed better use and allocation of IP addresses for medium-sized organizations.
The first proposal was to hierarchically allocate future IP address assignment, by delegating control of segments of the IP address space to Internet Service Providers.
This is why nowadays you can’t simply contact InterNIC and apply for an IP address. IP addresses are controlled by your local ISP.
Suppose you have an organization that needs no more than 2,048 host address (8 class C networks), and another that needs just over 4,000 (but no more than 4,096, or 16 class C networks). In this example neither a single Class C nor Class B range works. Since InterNIC designated ISPs as responsible for allocating IP addresses, we would contact our local service provider and they could assign the appropriate addressing scheme.
Supernetting involves dividing a Class B or Class C network into various other networks. Similar to subnetting, supernetting divides a single network address into various networks, but it splits the networks between different organizations. This makes for more efficient use of the IP address pool.
Keeping in mind our two requirements, let’s say we have a service provider who has the class C address range that begins with 192.24.0.0 and ends with 192.31.255.0. This range allows for 2,048 networks if supernetted. A supernetted route to this block of network numbers would be described as 192.24.0.0 with mask of 255.248.0.0. The service provider would allocate the address space as follows:
Client 1 needs no more than 2,048 (this allows for growth in the organization)
Allocate 192.24.0.x through 192.24.7.x (eight class C networks). The range of available IP addresses with this allocation are:
192.24.0.1-192.24.0.254 = 254 hosts
192.24.1.1-192.24.1.254 = 254 hosts
192.24.2.1-192.24.2.254 = 254 hosts
192.24.3.1-192.24.3.254 = 254 hosts
192.24.4.1-192.24.3.254 = 254 hosts
192.24.5.1-192.24.5.254 = 254 hosts
192.24.6.1-192.24.6.254 = 254 hosts
192.24.7.1-192.24.7.254 = 254 hosts
2,032 hosts
This block of networks is described by the supernet route 192.24.0.0 and mask 255.255.248.0. The supernet route allows for these 8 class C network to be one "network."
The second client needing no more than 4,096 addresses would get a similar series of class C address ranges that would include up to 16 different networks as shown:
192.24.8.1-192.24.8.254 = 254 hosts
192.24.9.1-192.24.9.254 = 254 hosts
192.24.10.1-192.24.10.254 = 254 hosts
192.24.11.1-192.24.11.254 = 254 hosts
192.24.12.1-192.24.12.254 = 254 hosts
192.24.13.1-192.24.13.254 = 254 hosts
192.24.14.1-192.24.14.254 = 254 hosts
192.24.15.1-192.24.15.254 = 254 hosts
192.24.16.1-192.24.16.254 = 254 hosts
192.24.17.1-192.24.17.254 = 254 hosts
192.24.18.1-192.24.18.254 = 254 hosts
192.24.19.1-192.24.19.254 = 254 hosts
192.24.20.1-192.24.20.254 = 254 hosts
192.24.21.1-192.24.21.254 = 254 hosts
192.24.22.1-192.24.22.254 = 254 hosts
192.24.23.1-192.24.23.254 = 254 hosts
4,064 hosts
When classful addressing first came about, companies that received a Class A address had over 16 million host address at their disposal. With only 126 allocated Class A networks there was a very large waste of prime host addresses.
This is where subnetting comes in. Breaking down one Class A network address into multiple subnetworks makes for better use of the available IP address pool.
Managing large networks of over 16 million hosts is challenging and there are not many networks this big. These large networks require many administrators and very good documentation, tracking, and communication.
Most networks will be smaller, with from one hundred to a few thousand hosts. These smaller networks are more manageable and do not require as many administrators. Some networks of only a few hundred workstations require only one administrator.
Computers can communicate only by a mix of 0’s and 1’s. Even though a TCP/IP address may look like 255.255.130.110, the computer understands this number only in binary form. Each number in 255.255.130.10 is considered an octet. An octet means it is made up of 8 bits, which are each a zero or a one. Having 4 octets means that an IP address is made up of 32 bits. Thus, an IP address is a 32-bit address.
The reason that IP addresses are shown in dotted-decimal form is so it is easier for humans to read. A number like 11111111111111111000001000001010 makes absolutely no sense to us. So to begin with we separate out a 32-bit address into 4 octets or four groups of 8 bits. Then our stream of 1’s and 0’s looks like this: 11111111.11111111.10000010.00001010. This is still hard to read so we convert the binary octets into a decimal number.
Each bit holds a specific value in each position. Figure 4-3 shows each bit position and the value if the bit is set to one.
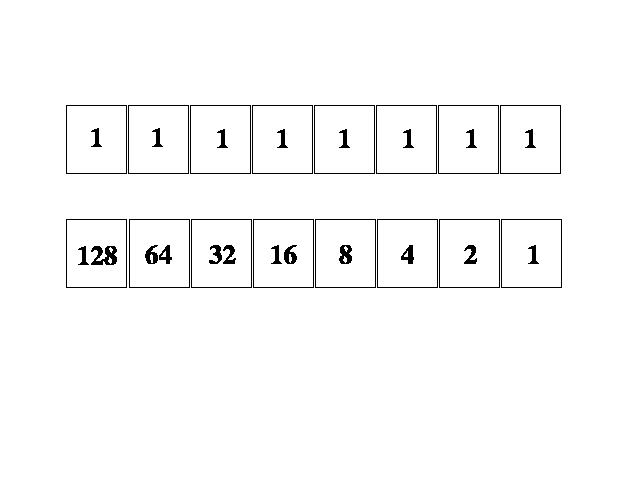
Figure 3: Bit Values
Figure 4-3 showd each decimal value. To make various decimal values you add the bit values together. If a bit is a 0, the decimal value is not counted. If the bit is a 1, then the decimal value is counted. The largest possible value for a decimal number in 8-bit form is 255. The smallest of course is zero.
Exercise 4-1 Converting a Decimal Number to Binary
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
137 |
|||||||
1 |
|||||||
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
X |
no |
no |
no |
9 |
|||
1 |
0 |
0 |
0 |
1 |
|||
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
X |
X |
X |
X |
X |
no |
no |
1 |
1 |
0 |
0 |
0 |
1 |
0 |
0 |
1 |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
If you a picture a stream of 32 0’s and 1’s as an IP address, there would be no way to easily understand how the decimal representation looks. Since each octet is separated by a period, we look at the decimal view that way also. The IP address 255.255.130.10 would be represented as 11111111.11111111.10000010.00001010 in binary. Converting a binary number to decimal is not a complicated process.
Exercise 4-2 Converting a Binary Number to Decimal
0 |
1 |
0 |
1 |
0 |
0 |
1 |
0 |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
If we put all one’s in the 8 available positions and add together all of the values, we come up with 255. This is the largest available 8-bit number. You will never see a 32-bit, 4-octet IP address witha number larger than 255. New versions of IP, however, may have numbers that are larger.
There may be times when you need to get more subnetworks out of your network. Depending on your requirements you can subnet in various ways. The default method of masking either one, two, or three octets can serve your purpose in most cases. However, you may have to borrow bits from one of the first three octets.
When defining your subnet mask remember that any bit with a one as a value is part of the network address. Also, any bit with a zero in the subnet mask is considered to be part of the host address.
When borrowing bits from an octet they have to be in a continuous block. That means there can be only certain values that fit into the subnet mask. Table 4-4 shows the representation of the contiguous values. The 1’s will always be to the left and the 0’s will always be to the right.
Binary |
Decimal |
00000000 |
0 |
10000000 |
128 |
11000000 |
192 |
11100000 |
224 |
11110000 |
240 |
11111000 |
248 |
11111100 |
252 |
11111110 |
254 |
11111111 |
255 |
Table 4: Borrowing Bits and Their Decimal Values
All 0’s will make the subnet mask one of the defaults. With the default subnet masks you have either the value 255 or the value 0 in each of your octets. The value 255 remember, is all 1’s in binary. So again if you have:
255.255.0.0
you then have:
11111111.11111111.00000000.00000000
in binary. This particular subnet mask means that the first two octets determine your network address and the last two octets determine your host address.
When borrowing bits from another octet you will have something like this:
255.255.224.0
which converts to:
11111111.11111111.11100000.00000000
in binary. What this means is that the first two octets, plus the first three bits in the third octet,determine your network address. So t the lastfive bits in the third octet and the entire fourth octet determine your host address. Take your time, ‘cause now it gets challenging.
There are of course advantages and disadvantages to stealing bits in an octet. With this process you can create more subnetworks in your network, and it can be easier to manage in some instances.
As you borrow bits, you increase the number of available subnetworks. This is great if you need to segment off certain divisions of your organization, or have remote offices spread out across the country or globe. The flip side to this is that the more networks you make available by stealing bits, the fewer hosts per subnetwork you have at your disposal. Keep this in mind when planning your subnetworks.
As you segment your network and organize each subnet, you will find that your network can become easier to manage. Troubleshooting can be easier if you are able to isolate probles to one particular subnetwork.
The flip side again involves numbers. If you have a network that has too many subnets to manage, this can make things tougher administratively.
There may be some disadvantages to subnetting if not properly planned and maintained. Proper planning and good documentation will help keep things managable.
As you steal bits from an octet to subnet your network, you find that the number of available networks grows. The other side to this of course, is that as you add networks you lose hosts per network. With each bit swiped, you lose a certain number of hosts per subnet.
We just want to reemphasize that if careful planning of your network layout isn’t done, then administering it can be a nightmare. Careful documentation of any changes and layouts is a must. As you administer the network, you will find that if too many subnetworks are implemented, you can cause yourself more work in the long run.
When planning and maintaining your network you have to know how to determine the subnet mask if you add a new office or location. There is a three-step process that is followed by most administrators:
| Determine the number of segments on your network. | |
| Count the number of bits needed to represent the number of segments needed. | |
| Push this number of bits to the high-order end and pad the remaining bits with 0’s. |
Once you convert the information to high-order bits, you can convert it back to decimal and you will have the IP octet information you need.
Exercise 4-3 Determine Number of Physical Segments
Figure 4: Athree- Subnet Network
X |
X |
X |
X |
X |
X |
3 |
1 |
0 |
0 |
0 |
0 |
0 |
0 |
1 |
1 |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
11000000
| 255.255.255.192-Class C | |
| 255.255.192.0-Class B | |
| 255.192.0.0-Class A |
Determining the range of subnet addresses and the subnet mask itself is easier than you think. If you remember that the borrowed bits are contiguous, conversion is easy.
Table 4-5 shows an easy way to remember what the octet values are for various subnets. The values of course are dependent on how many bits are being swiped.
Looking at Table 4-5, you see the bit positions numbered with 8 as the left-most bit. The bit values again are shown in row 2. To determine the decimal value of your subnet ID, you simply add together all the bits that are stolen in high order. The fourth row shows how many bits are stolen, and just above that in row 3 is the decimal representation.
We will explain this another way to make it clearer. This isn’t easy, so if you don’t have it yet, don’t worry, you will!
8 |
7 |
6 |
5 |
4 |
3 |
2 |
1 |
Bit position |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
Bit value |
128 |
192 |
224 |
240 |
248 |
252 |
253 |
255 |
Value w/high-order consecutive bits added |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
Number of stolen bits |
Table 4-5: Subnet Conversion Table
If you know the number of bits you want to swipe, there is a shortcut you can use to determine the number of networks and hosts.
Exercise 4-4 Planning Subnets Based on Configuration Needs
For this exercise you it would be handy to use the Windows calculator since it is available on the exam.
This method is known as the 2 to the power of bits - 2. You take the number of bits you want to swipe and take it to the power of two and then subtract 2. This will tell you how many network you can get by swiping that number of bits.
If you want to swipe, say 5 bits for your subnet, you would have the following:
25-2
This comes out to:
25=32
32-2=30
So in this instance you would be able to have 30 networks.
We subtract two because of the first and last option which is all 0’s and the last option which is all 1’s. These two are thrown out and this leaves us the possible number of networks.
To determine the number of hosts available, you take the binary value of the remaining host bits. The remaining host bits include every bit that is involved in the host address. If you are planning a class A network and are stealing bits from the second octet, you would count the remaining bits like this:
11111111.11110000.00000000.00000000 in binary
220-2 = 1,048,574 possible hosts per subnet
We take the value and subtract 2 again because any values with all 0’s or 1’s are disqualified.
Determining the number of subnets and hosts is an easy process once it is understood. The next challenge is to determine the subnet ranges. Planning and implementing your network requires a strong grasp on what your valid IP addresses are on each subnet and what their respective subnet address is.
Exercise 4-5: Determining the Number of Networks and Host Using 2n-2
For this exercise you should complete and have a good grasp on how to determine the number of bits you will use. This exercise is a reverse approach to determine subnetworks and host from a decision based on bit swiping. It is also a good idea to use the Windows calculator since the exam allows you to use it.
The biggest challenge that students face in regards to TCP/IP is determining the subnet address and then determining the valid range of IP addresses within each subnet. This concept is not as difficult as it looks. Once you determine how many bits you have to swipe, the rest is easy.
When you know your subnet mask for your network, you can take the subnet address (the octet where bits are swiped) and then start determining the valid subnet ranges. Let’s say that your subnet mask is:
255.255.224.0
You would take the octet that has the bits being split (or swiped as we’ve called it) and convert it to binary:
224 = 11100000
Since the swiped bits are always the bits with a one in their position you would take the right-most bit swiped and determine its value. In this example it is the third bit:
128 |
64 |
32 |
X |
X |
X |
X |
X |
1 |
1 |
1 |
0 |
0 |
0 |
0 |
0 |
128 |
64 |
32 |
16 |
8 |
4 |
0 |
0 |
For this example the right-most bit is 32. This gives you your first subnet address. If yourfirst two octets (in this example they would be the same throughout each subnet due to the subnet mask) are:
192.43
then your third octet would be:
32
for the first range of addresses. And your last octet for the subnet address is:
0
This gives you a subnet address of 192.43.32.0 for the first range of addresses. The first IP address would be 192.43.32.1. The last range is dependent on where the second range starts. To determine the second range we determine the next value by again using the first 3 bits (the swiped bits).
If you continue to move the bits to the next value you would find the following:
X |
X |
X |
X |
X |
X |
X |
X |
Row definition |
1 |
1 |
1 |
0 |
0 |
0 |
0 |
0 |
Swiped bits |
0 |
0 |
0 |
INVALID |
|||||
0 |
0 |
1 |
Value is 32 |
|||||
0 |
1 |
0 |
Value is 64 |
|||||
0 |
1 |
1 |
Value is 96 |
|||||
1 |
0 |
0 |
Value is 128 |
|||||
1 |
0 |
1 |
Value is 160 |
|||||
1 |
1 |
0 |
Value is 192 |
|||||
1 |
1 |
1 |
INVALID |
|||||
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
Bit value |
Again the first and last values represented by all 0’s or all 1’s are thrown out. The values you end up with in this example for subnet addresses are:
| 192.43.32.0 | |
| 192.43.64.0 | |
| 192.43.96.0 | |
| 192.43.128.0 | |
| 192.43.160.0 | |
| 192.43.192.0 |
This gives you six possible subnets when 3 bits are swiped. Going through our shortcut formula of 23-2 we find an answer of 6. This is a good way to double check our calculations.
We know that the IP addresses ending in zero on our network are the subnet addresses. The values ending in 255 are also thrown out due to our all zero’s and all one’s rule. Knowing this we can determine the ranges within each subnet:
| 192.43.32.0-192.43.32.1-192.43.63.254 | |
| 192.43.64.0-192.43.64.1-192.43.95.254 | |
| 192.43.96.0-192.43.96.1-192.43.127.254 | |
| 192.43.128.0-192.43.128.1-192.43.159.254 | |
| 192.43.160.0-192.43.160.1-192.43.191.254 | |
| 192.43.192.0-192.43.192.1-192.43.223.254 |
Reading through this you may have noticed a pattern developing. When we determine our first subnet address by using the right-most swiped bit, we can then make that the multiplier to determine our remaining subnets.
Again we borrow three bits so we take:
128 |
64 |
32 |
X |
X |
X |
X |
X |
1 |
1 |
1 |
0 |
0 |
0 |
0 |
0 |
128 |
64 |
32 |
16 |
8 |
4 |
0 |
0 |
Since 32 is the right-most bit swiped, it is then our first subnet and our multiplier. You take the multiplier and add it to the last value until you reach the subnet mask octet value. In this case the subnet mask octet we are concerned with is the third, or 224. Let’s look at this:
Starting value: 32
Add multiplier: 32+32=64
Add multiplier: 64+32=96
Add multiplier: 96+32=128
Add multiplier: 128+32=160
Add multiplier: 160+32=192
Add multiplier: 192+32=224 (not counted since it matches our subnet mask value)
This gives us the different subnet addresses. We put the network octets in front:
Another way to look at this is to multiply by the right-most swiped bit. Take 32 and multiply by 1, then 2, then 3, and so on. Continue until you multiply the swiped bit by the value equal to the number of networks. You can again use the 2n-2 shortcut to determine the number of networks. With 3 bits the value is 6 networks. You then multiply the right-most bit swiped by 1 and continue up to 6 like so:
32 X 1 = 32
32 X 2 = 64
32 X 3 = 96
32 X 4 = 128
32 X 5 = 160
32 X 6 = 192
We see the same values again for our various subnets.
Now that we know how to determine the number of subnets based on the swiped bits and how to determine the various ranges within each subnet, we need to know what the basic values are within subnets. Each class has a certain number of networks and hosts available with each available subnet mask. If we memorize this information, it makes administration in the real world and the TCP/IP Exam much easier.
Exercise 4-6: Troubleshooting Subnet Mask Errors
For this exercise you will need to have scratch paper or preferably a grease marker or something to erase and rewrite easily.
| Subnet 1: 210.210.128.0 | |
| Subnet 2:210.210.96.0 | |
| Subnet 3:210.210.64.0 | |
| Subnet 4:210.210.32.0 | |
| Subnet Mask of: 255.255.224.0 |
| Subnet 4:210.210.43.12 | |
| Subnet 3:210.210.100.192 | |
| Subnet 2:210.210.110.210 | |
| Subnet 1:210.210.126.4 |
With Class A networks the valid network ranges are from 1.x.x.x to 126.x.x.x. When subnetting your network you will receive one or a series of network IDs from your local ISP. Once you receive this information, you can subnet your network. If you are using a firewall on your network, you could operate with one IP address for the Internet and then choose your addressing scheme for your network. The value of 127 is not used with standard IP addressing. This is reserved for loopback and diagnostic functions. This is a Class A octet, but not a valid IP octet.
The default subnet mask for a Class A network is 255.0.0.0. Again, this means that the first octet determines the network and the remaining octets determine the host address. Class A networks consist of only 126 available subnets in classful routing.
When using a Class A network subnet you will subnet with the second octet, and with one scenario you will use the third octet (see below). The octet values for subnets whether they are A, B, or C class networks are the same, just in different positions. Table 4-6 shows the breakdown of the various subnet masks, the available number of subnets and hosts, and how many bits are borrowed in each instance.
| Number of Subnets | Subnet mask | Number of borrowed bits | Number of hosts |
| 0 | Invalid | 1 | Invalid |
| 2 | 255.192.x.x | 2 | 4,194,302 |
| 6 | 255.224.x.x | 3 | 2,097,150 |
| 14 | 255.240.x.x | 4 | 1,048,574 |
| 30 | 255.248.x.x | 5 | 524,286 |
| 62 | 255.252.x.x | 6 | 262,142 |
| 126 | 255.254.x.x | 7 | 131,070 |
| 254 | 255.255.x.x | 8 | 65,534 |
Table 6: Range of Valid Class A Subnets Using Bit Swiping
As you look at Table 4-6 you notice that with Class A bit swiping we can potentially have a Class B subnet mask. In other words we may end up swiping all 8 bits of the second octet. With this option we get 254 available subnets. The most you could have originally was 126. This is good for large organizations that have too many locations to use a standard Class A subnet mask of 255.0.0.0. As long as they do not go over the 65,534 hosts within each subnet they can use a Class B subnet mask and achieve some unique results.
With a Class B network the IP ranges are from 128.x.x.x to 191.x.x.x in classful routing. Again, the first octet of 127 (Class A) is not used, as it is for loopback and diagnostic testing.
The default subnet mask for a Class B network is 255.255.0.0. This means that the first two octets determine the network and the remaining two octets determine the host address. Class B networks consist of 16,384 available subnets in classful routing.
When using a Class B network subnet you will subnet with the third octet, and in one scenario you will use the fourth octet. Again, the octet values for subnets whether they are Class A, B, or C networks are the same, just in different positions. Table 4-7 shows the breakdown of the various subnet masks, the available number of subnets and hosts, and how many bits are borrowed in each instance.
| Number of Subnets | Subnet mask | Number of borrowed bits | Number of hosts |
| 0 | Invalid | 1 | Invalid |
| 2 | 255.255.192.x | 2 | 16,382 |
| 6 | 255.255.224.x | 3 | 8,190 |
| 14 | 255.255.240.x | 4 | 4,094 |
| 30 | 255.255.248.x | 5 | 2,046 |
| 62 | 255.255.252.x | 6 | 1,022 |
| 126 | 255.255.254.x | 7 | 510 |
| 254 | 255.255.255.x | 8 | 254 |
Table 7: Range of Valid Class B Subnets Using Bit Swiping
Exercise 4-7: Entering Ranges of TCP/IP Addresses for A Subnet
Masks
For this exercise paper and pen will be needed.
255 |
255 |
192 |
0 |
|
11111111 |
11111111 |
1100000 |
00000000 |
|
| 00 | INVALID |
|||
| 11 | INVALID |
210.110.x.y 210.110.a.b-210.110.c.d
210.110.x.y 210.110.a.b-210.110.c.d
As with Class A addressing using Class B subnets, Class B addressing will take advantage of a Class C subnet mask if all eight bits are swiped. The nice thing about this option is that your hosts and subnets are equal. This is the way to get a balance between your hosts and subnets.
With Class C networks the valid network ranges are from 192.x.x.x to 223.x.x.x. Anything beyond 223 is considered Class D and Class E, which currently aren’t used in Windows networking.
The default subnet mask for a Class C network is 255.255.255.0. Again,this means that the first three octets determine the network and the fourth octet determines the host address. Class C networks consist of 2,097,152 available subnets in classful routing. This sounds great at first, but within each subnet you can have only 254 hosts. Organizations nowadays are likely to have a lot more than that, but not as many as 65,000 with a class B address. This is where supernetting comes into play as we will seeshortly.
When using a Class C network subnet you will subnet with the fourth octet. Again, the octet values for subnets whether they are Class A, B, or C networks are the same, just in different positions. Table 4-8 shows the breakdown of the various subnet masks, the available number of subnets and hosts, and how many bits are borrowed in each instance. With Class C bit swiping you can have a situation where you only have the ability to have 2 hosts per subnet. Planning and careful consideration are essential.
| Number of Subnets | Subnet mask | Number of borrowed bits | Number of hosts |
| Invalid | Invalid | 1 | Invalid |
| 1-2 | 255.255.255.192 | 2 | 62 |
| 3-6 | 255.255.255.224 | 3 | 30 |
| 7-14 | 255.255.255.240 | 4 | 14 |
| 15-30 | 255.255.255.248 | 5 | 6 |
| 31-62 | 255.255.255.252 | 6 | 2 |
| Invalid | Invalid | 7 | Invalid |
| Invalid | Invalid | 8 | Invalid |
Table 8: Range of Valid Class C Subnets Using Bit Swiping
If you have an organization that has a medium-sized number of hosts and Class C licenses will not fill your needs, then you may try supernetting. Some organizations will waste a vast amount of Class B IP addresses and supernetting was devised to help keep the IP address pool from being carelessly used up.
You must understand subnetting in order to pass the TCP/IP exam. There are a few key items to remember when it comes to subnetting your TCP/IP network. Make sure you understand what the subnet mask does. It simply masks a series of bits to differentiate from the network portion of the address and the host portion of the address.
Once you are 100% sure on the basics of the subnet mask, then we get into bit swiping. Make sure to memorize the tables and have a good understanding of why there are a certain number of subnets for each mask and a certain number of hosts. Utilize the formula 2n-2; this is the quickest way to determine the number of networks and hosts when you swipe a certain number of bits. Remember the n is equal to the number of bits that you swipe.
Being able to determine ranges within your subnet is a must for successful networking. The TCP/IP exam will test you on this knowledge as well. Being able to look at a network diagram and determine what is wrong with the picture is a common scenario question. Be sure to hone up your skills on determining the subnet address, the subnet mask, and the various ranges of IPs within each. You have to be able to do these things in about any order, as well.
A basic understanding of supernetting is good, but not really required for the exam.
| The two-level hierarchy basically helps with routing the information to the appropriate host on a particular network. To do this you have to have a network address and a host address. | |
| Subnetworks come into play by having many smaller networks, so congestion isn’t an issue. | |
| You determine which bits or octets are used for the network address and which are for the host address by a term called masking. | |
| Classful addressing is based on the three distinct address classes: A, B, and C. | |
| A subnet mask basically masks or denotes a portion of the IP as the network address and the other as the host address. | |
| Don’t accept the obvious; use the ANDing process to determine if the hosts are on the same network. | |
| The three-level hierarchy adds a third component to the routing process, the subnet address, which takes a 4-octet IP address and divides it up three ways. | |
| Supernetting came about when medium-sized organizations were having difficulty with the standard addressing scheme. | |
| IP addresses are controlled by your local ISP. | |
| Supernetting involves dividing a Class B or Class C network into various other networks. | |
| The TCP/IP exam does not go into supernetting in depth. However, you do need a basic understanding of its purpose and how it affects IP address. | |
| Breaking down one Class A network address into multiple subnetworks makes for better use of the available IP address pool. | |
| An octet means it is made up of 8 bits, which are each a zero or a one. Having 4 octets means that an IP address is made up of 32 bits. | |
| Converting a binary number to decimal is not a complicated process. | |
| When borrowing bits from an octet they have to be in a continuous block. | |
| By stealing bits in an octet you can create more subnetworks in your network, and it can be easier to manage in some instances. | |
| Be prepared to determine how many hosts vs. networks you need when doing the masking stages of your subnetworking plan. | |
| There may be some disadvantages to subnetting if not properly planned and maintained. Proper planning and good documentation will help keep things managable. | |
| To define a Subnet Mask: |
| Determine the number of segments on your network. | |
| Count the number of bits needed to represent the number of segments needed. | |
| Push this number of bits to the high-order end and pad the remaining bits with 0’s. |